The Future is Here: Passkeys for Entra ID in Preview!
The tech world is buzzing with excitement as the long-awaited Passkeys for Entra ID finally rolls out in its preview phase last week! Gone are the days of cumbersome passwords, as Passkeys promise a seamless and more secure login experience. However, this preview unfortunately also shows that Microsoft has their work cut out for them. In the current state passkeys are very limited in setup and use and personally I had a lot of challenges getting it up and running. Keep on reading and I’ll tell you all about it!! Please note that passkeys are in preview and the information in the article can change at any time.
What are Passkeys?
Passkeys are a form of authentication, developed through the FIDO2 alliance, with the goal to replace traditional passwords for better security and ease of use. They use public key cryptography, meaning they consist of a key-pair: A public key which is located in the service you want to log in to, and a private key which resides on your device you want to log in from. Since the private key never leaves your device, you immediately introduce a device-dependency, unlike traditional passwords which works from any device in the world if you know it or can guess it.
In order to log in to a website using a passkey, you need to prove your identity before you can initiate the passkey on your device. This is either using a PIN code (which only works on that specific device) or preferably a fingerprint-scan or facial-scan with your web camera. Though not available in this preview, on a Windows 10/11 device your passkey could be stored in the Local Security Authority (LSA) database and protected with Windows Hello which will enforce PIN or biometric depending on your setup. This would provide a very secure MFA method without depending on any additional devices. With Passkeys you have an authentication method where your device and your biometrics combined proves your identity.
Every login with a passkey is only valid for a single login attempt, so passkeys are immune to attackers trying to re-use your login attempts to access your data. In layman’s terms: Think of it as a password which you don’t know and is changed automatically after every single login attempt.

Does this sound just like the way a standard FIDO2 key (like the ones from YubiKey, which is depicted above) works? Yes, it does. Passkeys are in fact, for all intents and purposes, a software version of a physical FIDO2 key. But instead of purchasing a physical key to insert into a USB-port, a passkey is stored a device of your choosing. This can be your phone, or even easier, the PC you are logging in from (not available in preview at the moment).
Why all the fuzz?
Passkeys are revolutionizing the way we approach authentication, offering a phishing-resistant method that could potentially eliminate the need for passwords entirely, depending on the environment. This advancement is a significant milestone for identity security within Entra ID/M365. Furthermore, it can potentially liberate users from the necessity of a mobile phone for multifactor authentication (MFA), as the device itself serves as one authentication factor, complemented by a PIN or biometric verification. Again, not available in the current preview unfortunately. It’s important to consider that certain user groups, such as young students in Norway’s elementary schools, or healthcare workers in certain scenarios, may not have access to mobile phones (or physical USB-sticks) for MFA. Passkeys offer a promising solution to secure their accounts effectively. In essence, passkeys in general provide: – Robust defense against phishing and replay attacks – No need for additional licenses – Compatibility with existing hardware, avoiding extra costs – A step towards a fully password-free environment, contingent on the system’s integration The introduction of passkeys could be a game-changer, especially for protecting vulnerable user groups and simplifying the authentication process.
Getting started with Passkeys in M365
First a quick word about the current limitations, as of April 2024
- Passkeys can only be stored in the Microsoft authenticator app on android and iOS devices.
- Minimum versions:
- Android 14
- iOS 17
- Android has setting when the authenticator app must be set as the preferred provider for password, passkeys and accounts. Which can cause issues (keep reading)
- Nothing official on android models yet, but it does not seem to work on Google Pixel devices (which I have 🙁)
So how do you get started? By following 3 easy steps:
- Prep your tenant to enable passkey as an authentication method
- Enroll passkeys on your device
- Use passkey to log in
Here are the steps in more details:
Step 1: Prep you tenant
In Entra ID Passkeys are not enabled by default, so an admin needs to add 2 AAGUIDs in Authentication method to enable passkeys as an authentication option.
As an admin: Open the Entra ID portal and select Protection -> Authentication methods (or use this direct link) and enable and select “FIDO2 Security key” for your users who should be able to set up passkeys as their authentication method. 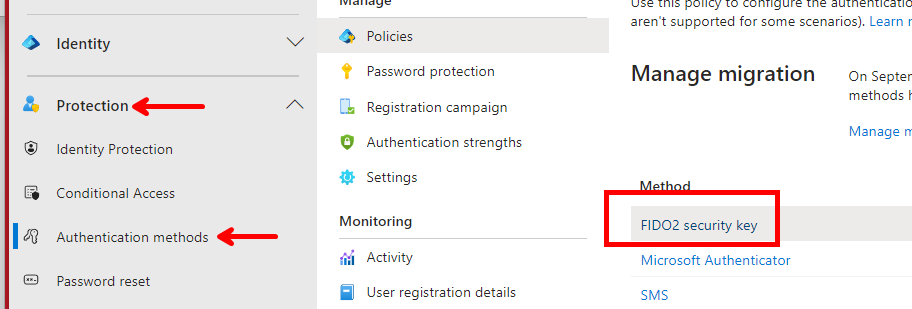
Select “Configure” in the top and if “Enforce key restrictions” is not set, you need to temporarily select “Yes” in order to add the AAGUIDs, you can set it to “No” afterwards of you wish.
If you already have AADGUIDs configure you must make sure they remain or else your existing FIDO2 keys will stop working. When you’re done, click “Save” at the bottom. Add “de1e552d-db1d-4423-a619-566b625cdc84” to support android devices, and “90a3ccdf-635c-4729-a248-9b709135078f” to support iOS devices.

Entra ID is now prepared for passkeys, and users can now enroll them on their android/iOS devices.
Step 2: Enroll passkeys on your device
This is the part when things quickly becomes complicated and confusing as things are today, and I’ll try to explain why. The tenant is prepared for passkeys and now an end-user wants to enroll passkeys on his/her android device. The procedure is as follows:
- On the end-users client: The user must open a web browser and navigate to aka.ms/mfasetup, alternatively navigate to myaccount.microsoft.com, login with their work-account and select “Security info“.
- Select “Add sign-in method” and “Passkey in Microsoft Authenticator (preview)” should be available, select it
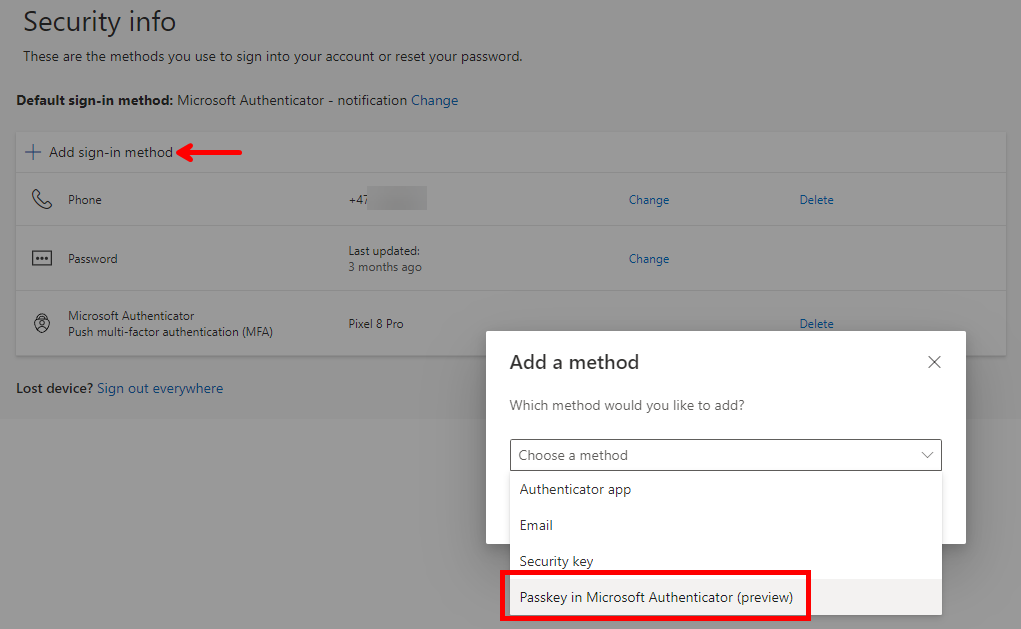
- A message pops up saying you need to download the authenticator app and your device must be at least Android 14 or iOS, click “next” when you’re ready to proceed.

- Next select which device, in this case Android
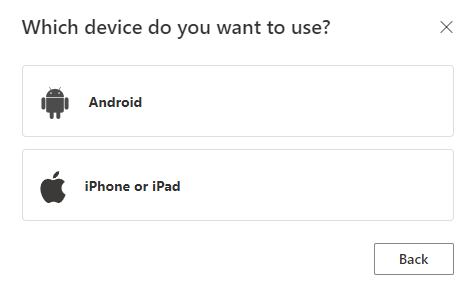
Now you see instructions on how to configure your android device to prefer authenticator as your passkey provider. These instructions are unfortunately too vague as different vendors of android devices have different name/settings. I struggled a bit here to find the correct setting on my Pixel 8 Pro and a Samsung S22 phone. More on that later. Select “Continue” when you’re set.
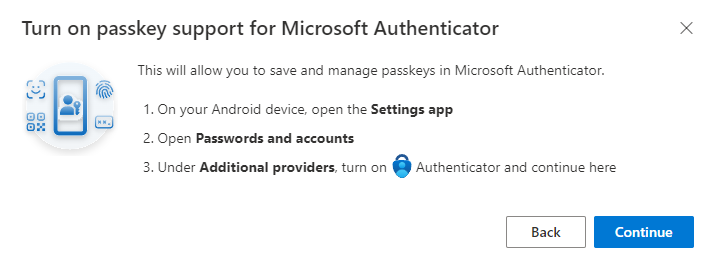
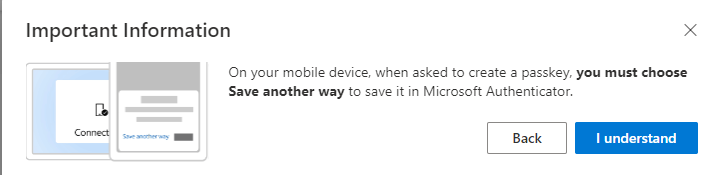
- 2 new popups: 1 saying you must scan a QR code with the phones native QR scanner, 1 saying you must select “Save another way” on your mobile device.
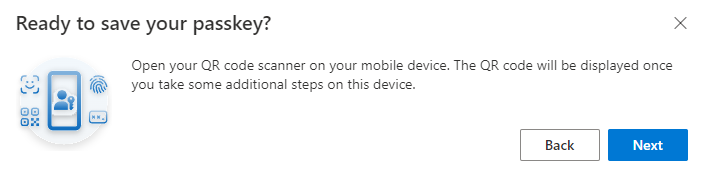
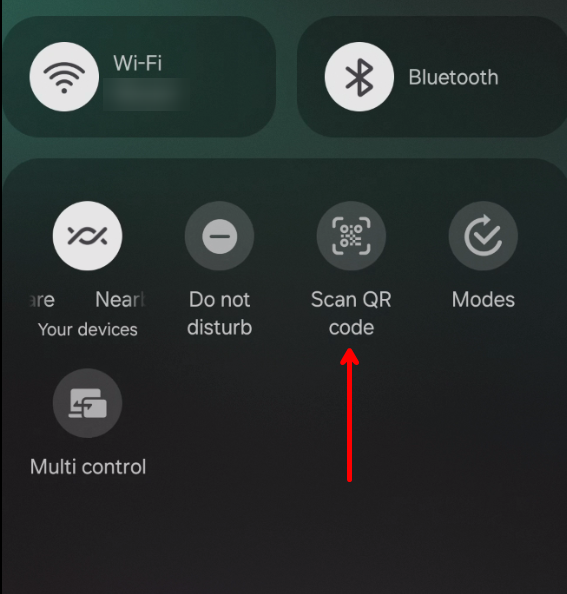
- On your phone, you must select the built-in QR scanner, do not scan the QR code using the authenticator app.
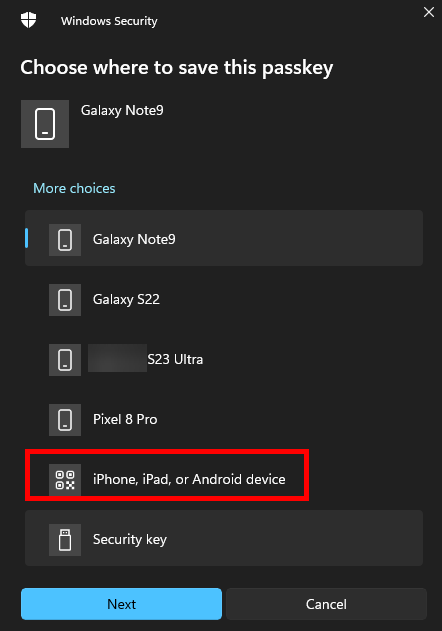
- You will be asked where to save your passkey, select “iPhone, iPad, or Android device“
- With the phone: Scan the QR code on the screen and the phone will show a message to “Skip the QR code next time?” which is an ambiguous way to ask if you want to save the passkey on your phone, tap OK.

- The phone will then ask to create a passkey and save it in the Authenticator app. Tap Create to do so. If the phone offers another app than the Authenticator here, the passkey will not work (I have tried so you don’t have to).
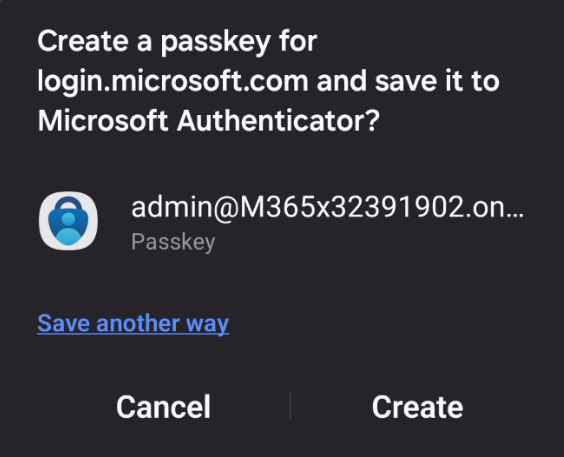
- The passkey will hopefully save successfully, and you’re prompted to give it a display name to identify it later. Give it whatever name you want and select “Done“.
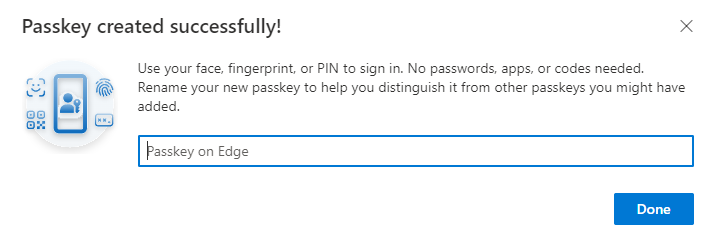
The passkey is now listed as an authentication method.
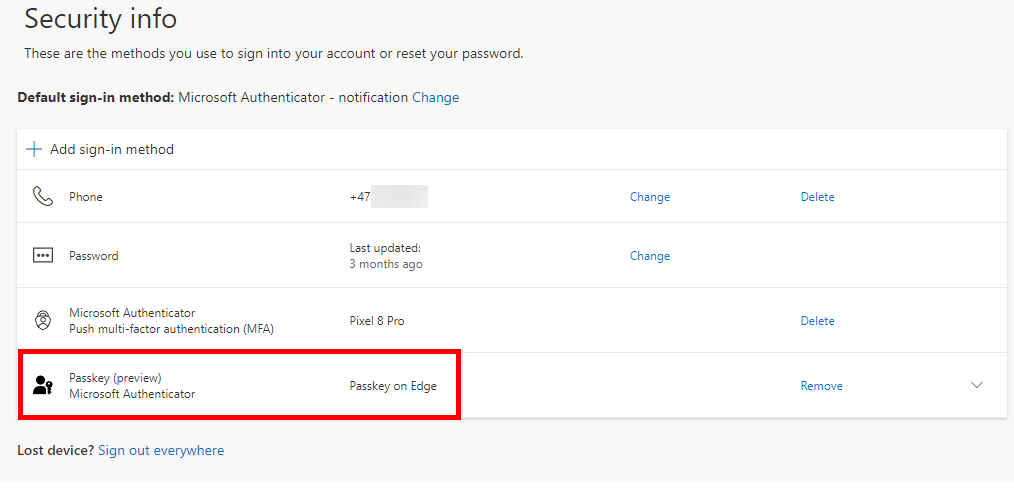
Step 3: Logging in using passkeys
So, it’s time to test the passkey.
I’m opening a web browser and navigating to Entra ID adminportal, and here I select my username “admin@….” 
Instead of entering my password I select “Use your face, fingerprint, PIN, or security key instead” 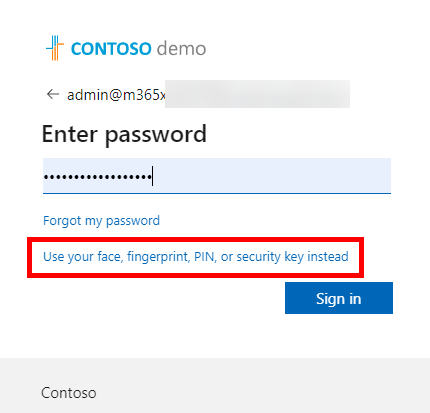
Windows then asks me where the passkey is saved, in this case it’s the Galaxy S22 so I select it and click next. 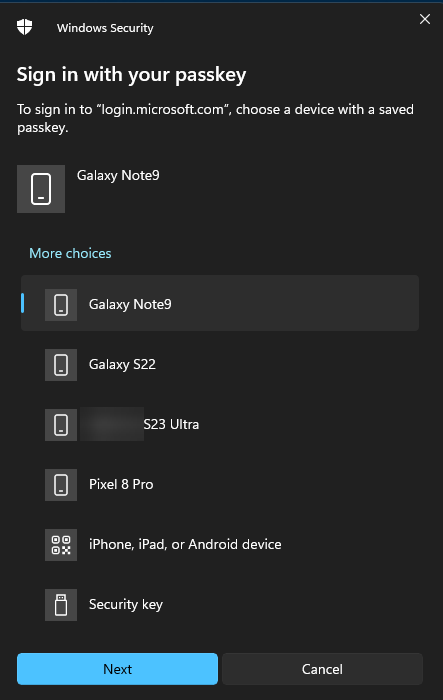
Windows then sends a push notification to the selected device, in order to initiate a logon with passkey.
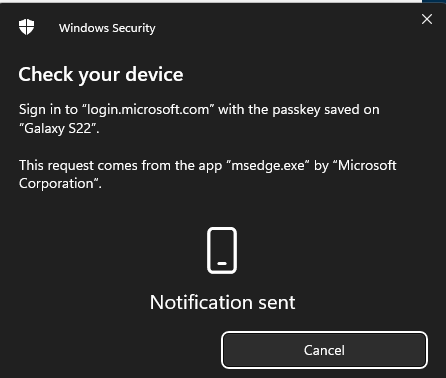
On my phone, I get the push notification and I’m asked to select which user I try to log in with. Notice that all passkeys on the device are displayed here, across all tenants not just he one you try to log in to. I select “admin@…” for the correct tenant, and I must use my fingerprint on my phone to verify my identity.
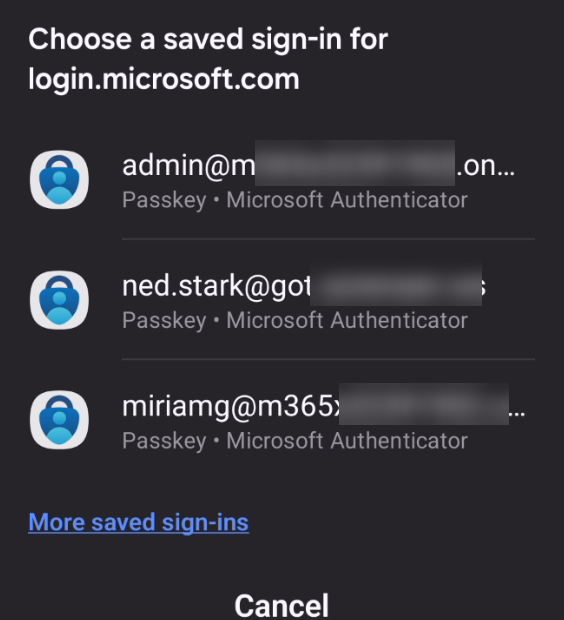
And that’s all I need to log in. No password needed!
My own experience so far
Friday morning 12th of April I learned that the preview was live. And I spent 2 days, using 4 different phones on 3 different tenants before I managed to get it working. So long story short:
Phone issues
I was plagued by “Something went wrong” error on my phone immediately after I tapped “OK” on Skip the QR code next time? window, both on my Pixel 8 pro and on my older Samsung Galaxy Note 9. The Note 9 only had Android 13 available, so that’s understandable, but my Pixel 8 Pro ticked off all the prerequisites and should work without issues. So I spent a lot of time troubleshooting different settings, and tried different tenants if there were other settings that somehow interfered. But in the end I got nowhere. There were no information in the logs in Entra ID and I found no clues on the phone or in the authenticator app. 
I borrowed my wife’s Galaxy S23 and faced a new issue. Despite altering the settings on her device, I couldn’t get it to suggest using the authenticator app to save the new passkey. It stubbornly demanded that the passkey be kept in Samsung Pass, Samsung’s equivalent of Google Wallet, which inevitably led to failure. No matter the adjustments made, the phone was programmed to default to Samsung Pass for storing passkeys, and I suspect it was because she already had started to use Samsung Pass. I did however, find a used Samsung Galaxy S22, which was reset to factory default. So after charging it, booting it up and installed Android 14 and various patches, I finally got it working!
RDP issues with webauthn
Another issue I found is that passkey barely work over RDP, and since I have different virtual machines for different customers, this is a showstopper for me personally. I use Remote Desktop Connection Manager for Sysinternals daily because I have labs, demos and dedicated VMs where I log on to customers from. Passkeys does not work with RDCMan at all, neither to set up or to log in with.
My first instinct is that this is because RDCMan can’t use “Web authentication” (webauthn) which is a core component to FIDO2/passkeys. So I checked for alternatives. “mRemoteNG” did not support webauthn as I could see, but “Remote Desktop Manager” (RDM) from Devolutions do. But it did not work using RDM either. So with a sigh I went to the native RDP client in Windows but even there I had issues.
After quite a bit of trial and error I made it work with these settings:
- Make sure the user is logged out of the target computer. Not disconnected, but logged out completely
- Run RDP session to the “admin session”, I.e. run “mstsc /admin“
- Make sure, before you connect, that “Webauthn” is being forwarded from local device:
- in the client “Local resoruces” –> “More” –> Select “Webauthn (Windows Hello or security keys)“
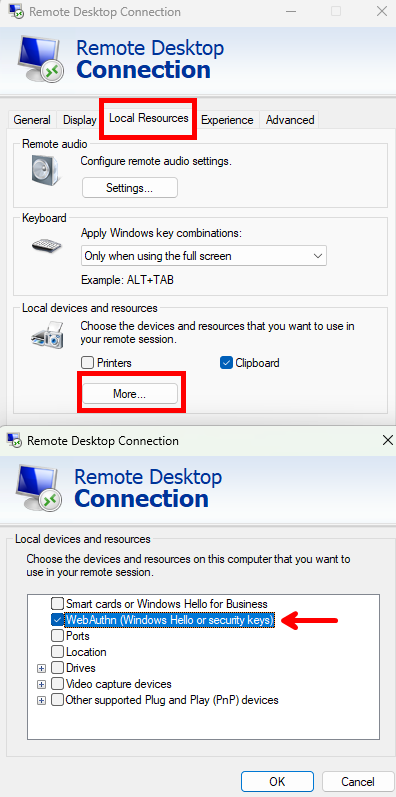
- You also must connect to the client with these settings both to configure passkey, and every time you want use the passkey for logging in.
- I assume Citrix sessions, M365 CloudPC and AzureVMs face the same issue, but I haven’t been able to test this.
So as of today, it’s not viable at all for me, unfortunately.
The good:
- Passkey is a free alternative which is resistant to spoofing and replay attacks. I wrote more about it in the intro.
- When it’s set up properly, then it works very smoothly
The bad:
Yes, I know you’re thinking that it is only in preview so far, but still:
- We’re forced to store the passkey in the authenticator app on a mobile device and this seem meaninglessly restrictive.
- We have had passkeys for a long time now from other vendors (Visma, GitHub, Ebay, outlook.com and many others) where you simply store the passkey directly on the Windows device you’re using.
- Slightly high requirements to Andriod/iOS versions
- Vague and imprecise directions to configure the mobile device to store passkeys
- Only viable on local device, no RDP
- Push notification during login should be filtered to relevant tenant. As a consultant with many customers this list will be HUGE if it stays unfiltered.
- again… why can’t we store the passkey in Windows directly?? Why? It makes a such huge difference in both user convenience and use cases.
Conclusion
If I’m going to briefly evaluate Passkeys as of today I feel I should repeat what I say about Copilot: “When the product is finished, it WILL be really, really awesome!” And that is both anticlimactic and disappointing. Both because passkeys aren’t a new technology, it’s being used many other places where it is so much easier and quicker to configure and use. And also because after months of having Passkeys in private preview, I honestly expected Microsoft to have come further than what we see today.
But Passkeys are still the best way yet to finally be able to seriously push for password-free environments, and without having to purchase licenses or hardware tokens. When passkeys in Entra ID are as flexible and easy to use as (for example) passkeys in GitHub, then I will never go back to MFA over Authenticator app which is my default today.
Discover more from Agder in the cloud
Subscribe to get the latest posts to your email.

