Summer is finally here and for most people it’s vacation time very soon. But many companies experience that some of their employees wants to be able to access their resources while abroad. This means you need to wither reject their request or poke a hole in you geoblock-rules in your Entra ID Conditional Access. (You DO have geoblock-rules right?)
So I’ll set up this scenario to demonstrate the possibilities with Entra ID Access Packages:
- Normally logging in from outside Scandinavia is blocked in your environment
- Users traveling outside Scandinavia (for example other European countries) on vacation should temporarily be able to log in.
- We want to automatically remove the access from outside Scandinavia after a set amount of time.
- We don’t want to open logins from every country in the world
- We still want to enforce other security measures like MFA for the users on vacation.
Access Packages to the rescue! 🥳
Entra ID Access Packages allows you to control access to groups, Teams, applications and SharePoint sites in a flexible, but secure way. They can be assigned automatically, manually or upon request for a limited time or permanently. Combining Access Packages in Entra ID with Conditional Access gives us a very easy fix for this scenario without sacrificing security too much. Access Packages requires Entra ID P2 license for basic configuration, but more advanced features require Entra ID Governance license. Details are listed here.
An overview of Access Packages:
Resources are groups/applications/teams/etc, these are places into one or more catalogs. These catalogs are organized into one or more Access Packages and then made available to users through an Access Package Policy which states the requirements and limitations for users access.
Resources –> Catalog –> Access Package(s) –> Access Package Policy –> users or groups
Solution design
In this scenario my suggestion would be:
- Create a security group for users who should login from outside Scandinavia (which again is our default geo-block)
- Create an Access Package where users can request membership to this group for a limited time, and requests needs to be approved before access is granted.
- Define a list (aka “Named location”) of countries allowed to login from, outside Scandinavia. Remember, we don’t want to open up for the entire world.
- Change and create Conditional Access rule to allow group members to login to M365 from select countries outside Scandinavia.
Create a group and place it into a catalog
Just create a new security group in Entra ID. no specific requirements except to follow your naming standards
Then navigate to Identity governance and Entitlement management, here you will find both Catalog and Access packages.
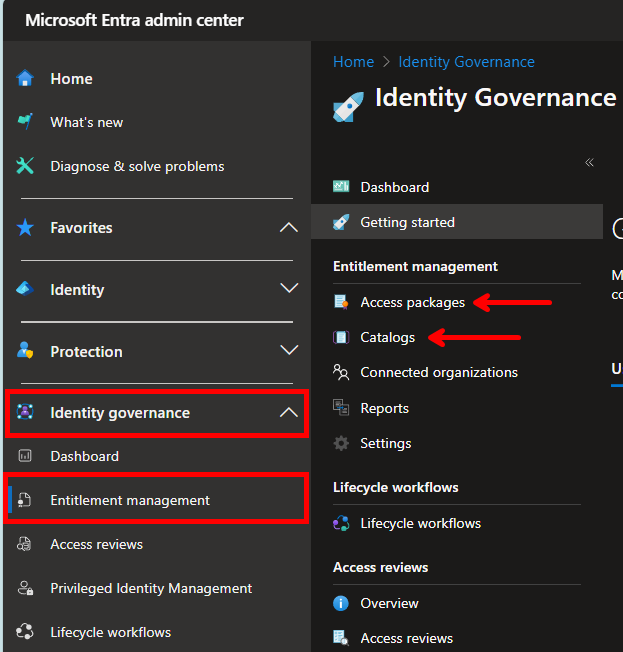
Select “Catalogs” and then “New catalog” in the top. Provide a name and description (this will be visible to end users) set “Enabled” to yes, and “Enabled for external users” to no. Then click Create at the bottom.
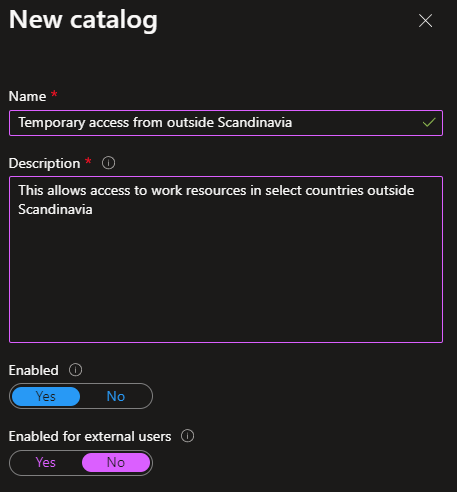
Doubleclick on the new catalog and select Resourcs on the left, Add resources in the top and add the group you created earlier so it appears in the list.
Create an access package for the catalog
Then to back to “Identity Governance” and select “Access Packages” on the left and “New Access Package” on the top.
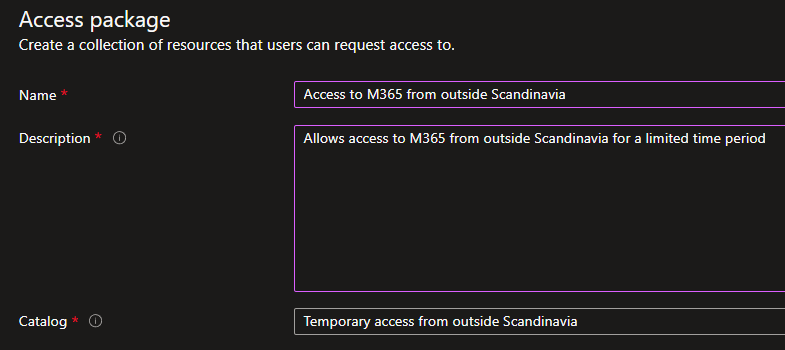
Basics:
Enter a name and description, keep in mind this is visible for the end user. Make sure you select the correct catalog.
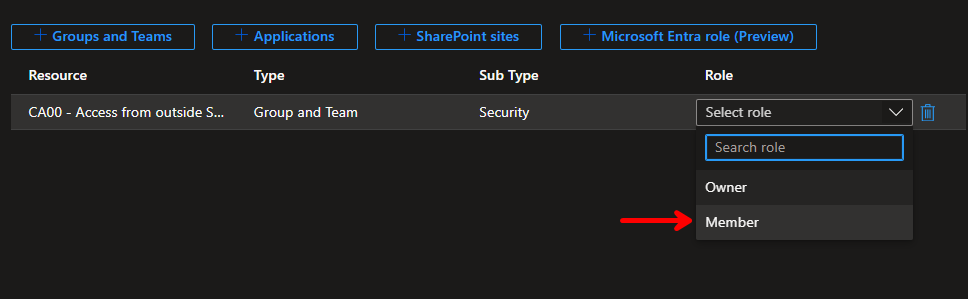
Resource roles:
Add the relevant group from before, make sure you select “Member” under “Role” to the far right.
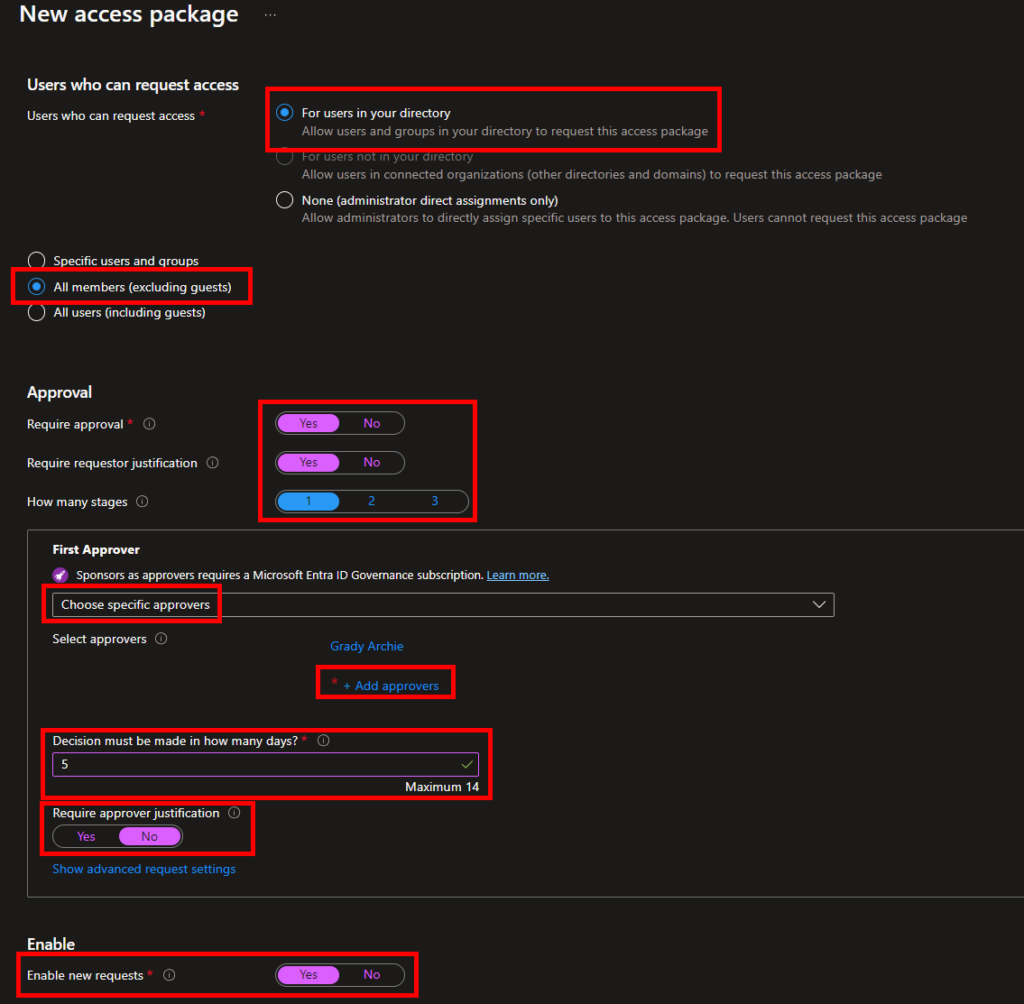
Requests:
There are a lot of options here, so I will present a suggestion but feel free to change the settings to suit your own needs. This will make up the Access Package policy as I mentioned in the start.
- Select “for users in your directory“, “All members (excluding guests)”.
- Require approval: Yes (if you select, users are automatically grated access when requesting)
- Require requestor justification: Yes (if users must write a reason why they should get access)
- How many stages: 1 (how many steps of approval, 1 is usually sufficient)
- First approver: Pick one or more persons to receive the request and approve/deny them, and how long the approver(s) have to respond. Note that the approvers do not require any privileged access whatsoever.
- Enable new requests: Yes (selecting “No” here will prevent users from requesting access)
Requestor information:
Click “Next“
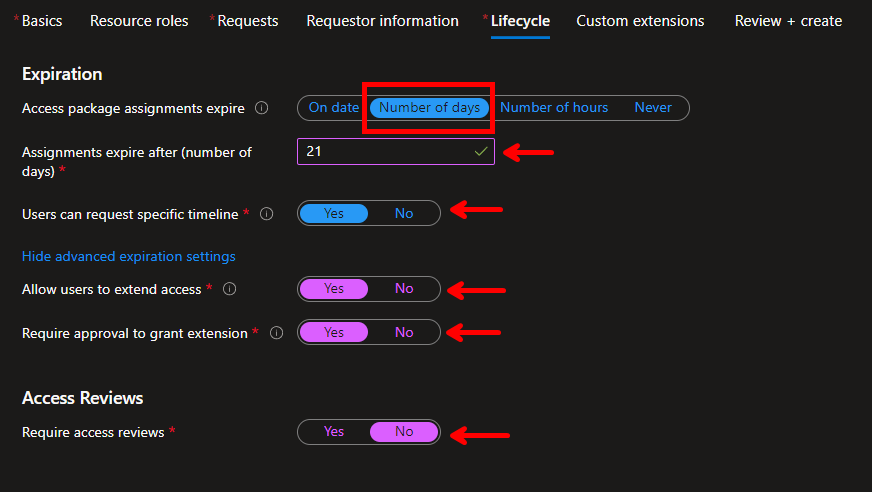
Lifecycle:
This is how long the access should last and if the user can extend their access.
- Access package assignments expire: “Number of days“
- Assignments expire after (number of days): 21
- Users can request specific timeline: Yes (This allows the end user to specify their access ahead of time, which is really useful in this scenario)
- Allow users to extend access: “Yes“
- Require approval to grant extension: “Yes“
- Require access reviews: “No” (you may want to set up access review but for this demo I will select No to keep this post somewhat short).
Custom extensions:
Click “Next“
Review + create:
Click “Create” in the bottom and you’re done here.
Named location and Conditional Access rules
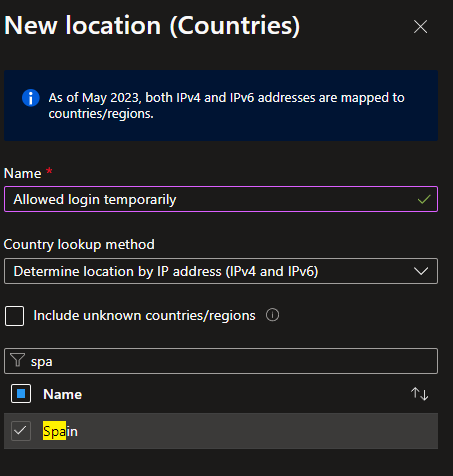
In Entra ID: Navigate to Protection and Conditional Access and Named location. Select “+ Countries location” in the top and add the countries you want to grant access to M365 from and click Create at the bottom.
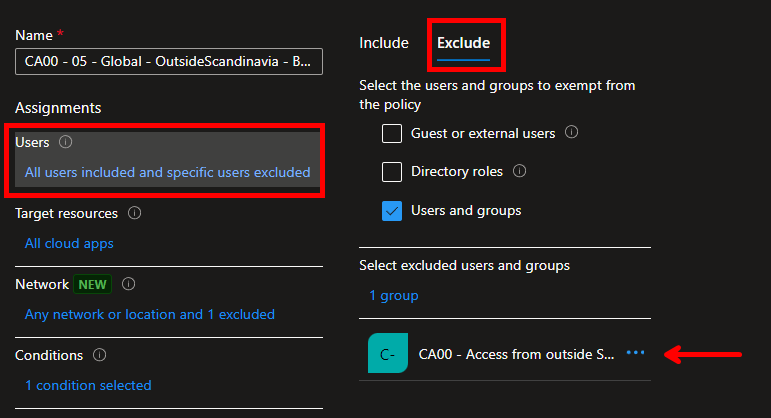
Select Policies on the left side and edit your current geo-block Conditional access rule. Exclude the group you created in the start from this rule.
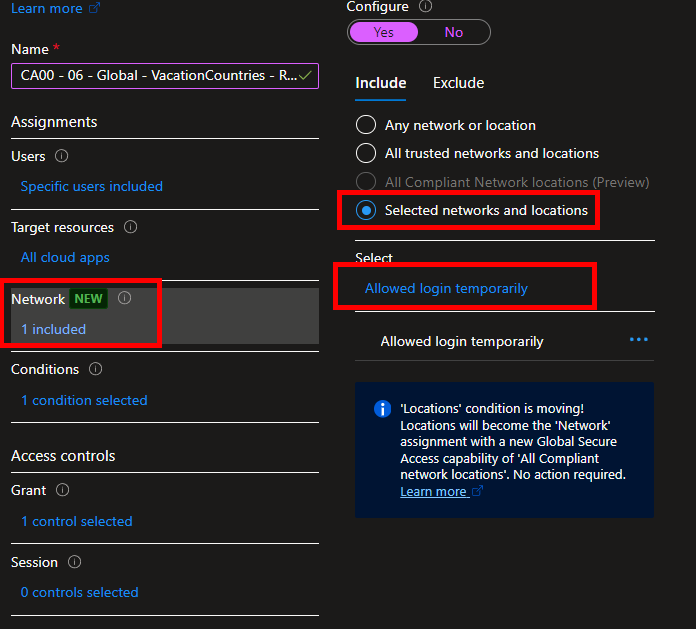
Create a new Conditional Access rule:
Users: The same group as you just excluded from the geo-block rule
Target resources: All cloud apps (You can specify specific apps to lock this further down, but I’ll do All cloud apps for demo purpose)
Network: Include Selected network or location and select the countries location you just created
Access control: Whichever requirements you have, I will select Require MFA for this demo.
Now, any users who are member of this group will be allowed to login to M365 from the countries specified using MFA. Now we just need the users to request access and approve/deny their requests.
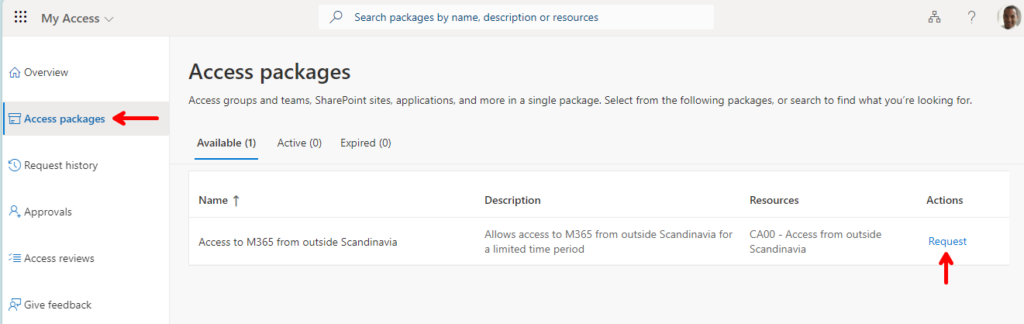
End-user access request
The end-user now only needs to log in to myaccess.microsoft.com and they will find “Access packages” on the left side along with the packages available to them. Here they click “Request” on the right side to request access.
Press Continue on the first screen and then they can specify when they want their access if they want to and provide their justification of required. Finally click “submit request“
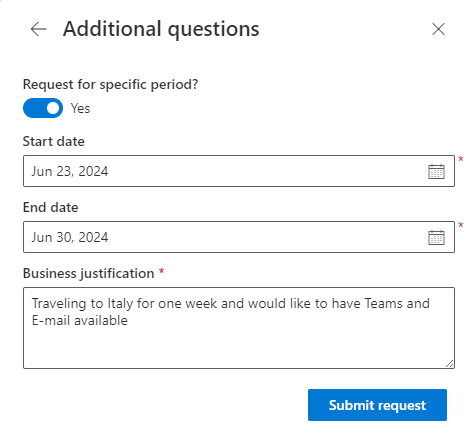
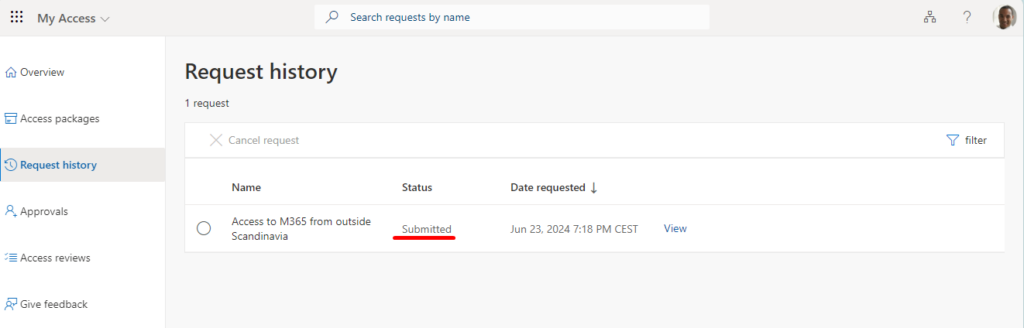
The request is now visible under “Request history” along with the status
Request approval
Again, the approvers do not need any privileged access. The system will handle the technical changes for them. They will receive an e-mail notification that they have a pending request.
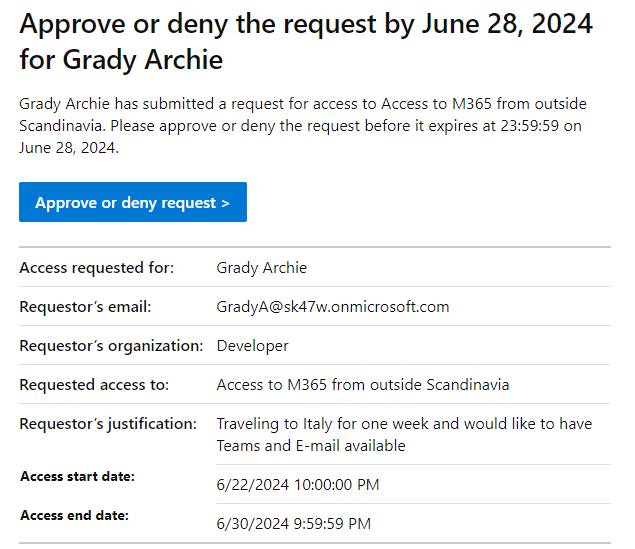
The e-mail has a link to the request, but they can also see their pending requests at myaccess.microsoft.com. Click “Review” on the right side to get started.
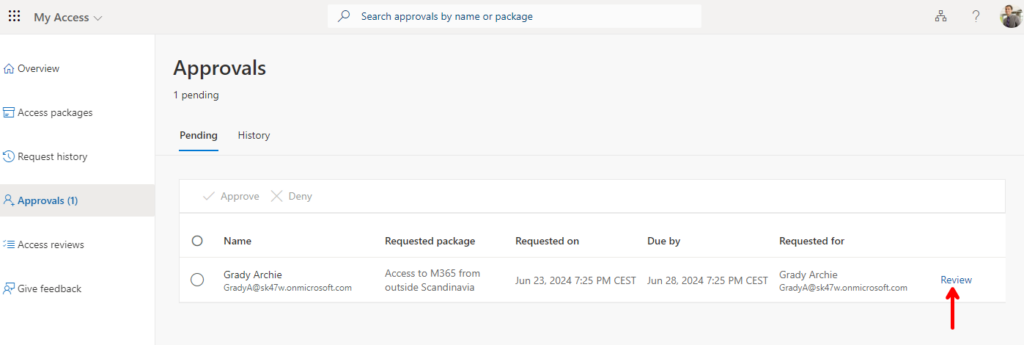
Here they can see all the information provided in the request and can select “Approve” or “Deny” and then click “Submit” in the bottom.
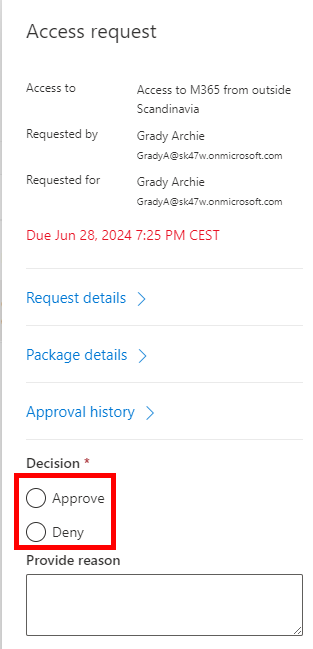
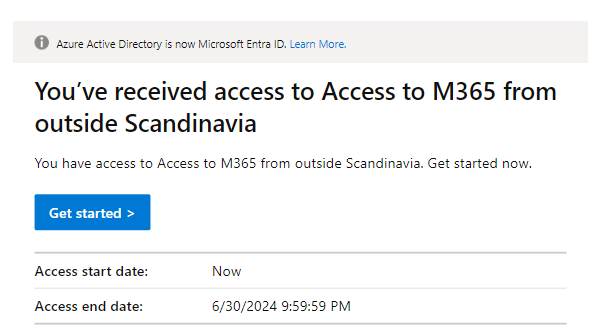
The end-user (requestor) will automatically receive an e-mail of the response and, if approved, automatically get access to the group for a limited time.
Conclusion
Entra ID Access Packages is a robust and adaptable solution for managing user access within an organization, and is an incredibly important tool in these copilot times we live in now. While this was a very simple and quick introduction, I hope you can see its flexibility and simple setup to provide temporary access for those employees who wants access to resources while travelling abroad.
I hope this post was useful, please keep you systems safe while you and your colleagues are on vacation. Wish you all a great summer! ☀️🌴
Discover more from Agder in the cloud
Subscribe to get the latest posts sent to your email.


