Passkeys in Entra ID is currently in public preview. I wrote a post about it just over a month ago, which you can read here, and I thought it is time to go through what’s happened with passkeys since then. Passkeys are still in public preview and I expect more changes will come soon, but this is my information and experience as of late May 2024.
Admin changes
A small change in Entra ID admin portal: You no longer have to add the AAGUIDs manually under the FIDO2 security key settings to add support for iOS and android-based Microsoft authenticator app. We now have a checkbox which will add them automatically for us.
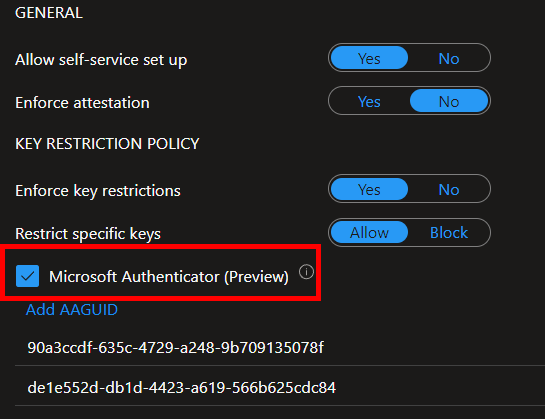
Android issues – fixed (?) ✅
I can finally create Passkeys on my Pixel 8 Pro! While there never were any official restriction on the make and model as far as I could see, I was previously only able to create and store passkeys on Samsung Android phones. This seems to have been fixed now. 😊 I have been told that passkeys are still unreliable on Android, but I have not experienced this myself.
RDP issues – fixed ✅
I use RDP every day so to me this functionality is crucial. Luckily, it now works great through RDP but remember that passkeys rely on the protocol “webauthn“. So your RDP client must be able to redirect webauthn if you want to use passkeys. I had to say goodbye to RDCman after many years as webauthn is not supported, and RDCman doesn’t seem to be updated anymore (I will miss you 😞). But I’ve gone back to Remote Connection Manager from Devolutions and it works like a charm. I no longer have to make sure I first am logged out of the target computer and connect to the console-session first, in order for Passkeys to work. As long as webauthn is redirected it just works. 😊
Device cleanup 👍
This is a tip I got from a friend and colleague Torstein Eriksen, a great guy who is very skilled (please pay him a visit on linkedin). After testing passkeys on several mobile devices they remain in the pop-up list depicted below, and this list can grow rather long if you do a lot of testing. The list is saved in the registry where you can locate your unwanted devices there and remove them. The registry path is Computer\HKEY_USERS\S-1-5-20\Software\Microsoft\Cryptography\FIDO\%your SID%\LinkedDevices
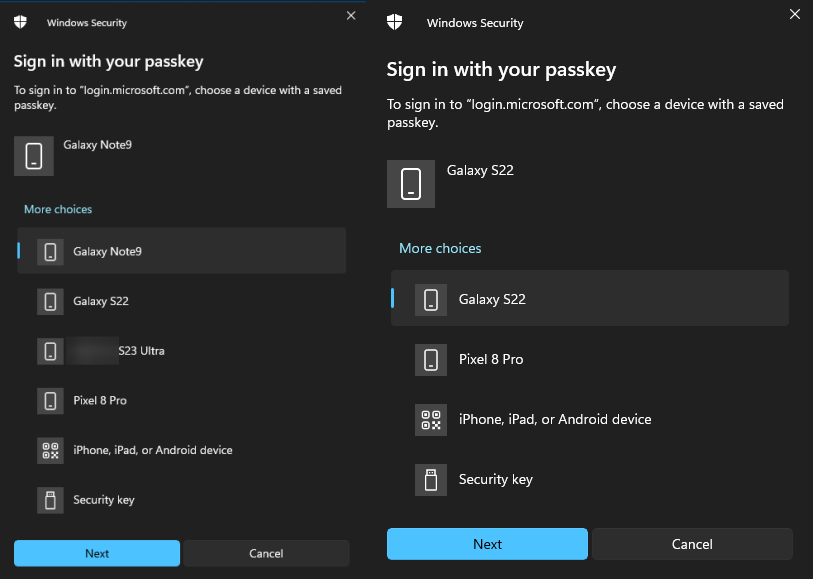
Filter needed
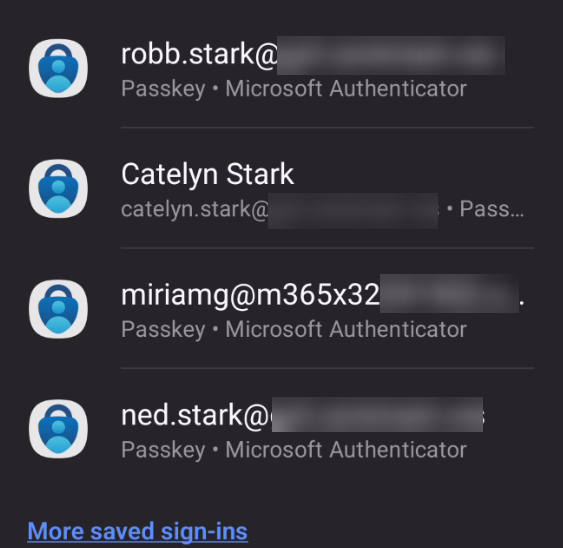
When you log in with a passkey, the prompt on your mobile device will list 4 passkeys stored in that devices authenticator app and if you have more, it will display a “more saved sign-ins” link (picture below). You need to manually locate the correct passkey to log in and tap it. This list should absolutely be filtered so it only displays the passkeys with the UPN matching the login attempt.
My (updated) thoughts so far 🤔
The good:
- Logging in with a passkey is still much more secure than traditional password+MFA as it not only makes a passwordless design possible, but passkeys are designed from the ground-up to be very resistant to phishing attacks. Phishing is one of our biggest security challenges today so this is a very big deal!
- Almost all of my negative points in the previous post has been fixed.😍 It now works properly through RDP and I can actually use my own phone to store and use passkeys with.
The bad:
- Passkeys still seem buggy and I find it a little unreliable. In one of my tenants passkeys just won’t register despite using the same settings which works in other tenants.
- The onboarding process is still cumbersome, and I would not recommend any large scale testing until this has been improved.
- Passkeys in Entra ID are not as user-friendly as it should be, in both onboarding and in use. I think ordinary end-users will struggle with too many steps to set up with imprecise instructions and not as easy login process as it should be.
- The absolutely most important flaw with the current design is still the dependency on the Microsoft authenticator app on Android/iOS for passkey storage. This has, in my view, a couple of very important drawbacks:
- First of all, this introduces an unnecessary dependency of an Android or iOS device which in addition has to be pretty modern too (Android version 14 and iOS version 17 minimum). And there are large amounts of end-users who can’t meet this requirement. Most notably in my work are all the elementary school children downwards to the age of six years old. These children don’t have access to cell phones at all, and we really need to find a proper way to protect their accounts.
- Second, this onboarding process is not user friendly at all, and if we want users to embrace and use passkeys, they have to be easier to use than password+MFA. Keep in mind that onboarding users is much easier if you appeal to convenience in their day-to-day work. The fact that logging in with a passkey is much more secure is important to us technical IT-nerds, but for an ordinary user this fact will mostly be ignored. But try telling the users that they can log in without remembering their password, and without entering a code on their mobile phone. You will be their new best friend and once they get a taste of passkeys they will never ask to go back to password+MFA again. This is what we need and what we want!
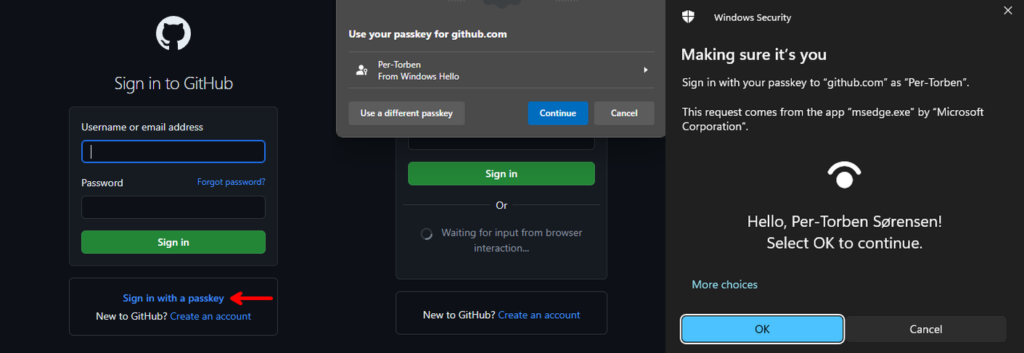
- Last but not least: There are several websites who has implemented passkeys in what I strongly think is a better way, and my go-to example is GitHub where you can simply request a passkey in the settings-menu and it can store it directly on your Windows device. It takes 3 clicks and it’s done. When you later want to use the passkey for logging in, you can simply select to login with a passkey and use Windows Hello to active the passkey stored on your local computer. For me, I just need to look straight into my webcam and I’m logged in, I don’t even have to type my username! Look at the screenshot below. It can’t get any easier than this, and end-user would LOVE to have this as a login method!
Conclusion
With the improvements in the preview since April, passkeys has finally given me some real-life value and when it works I really enjoy it. There are in my opinion not many downsides to passkeys in the preview now, but the downsides which remains are pretty important and can be very impactful. Nevertheless, passkeys are here to stay and they will no doubt provide a massive improvement to identity security. I strongly recommend that you start looking into it, but beware of the limitations in this implementation in Entra ID and I suggest start with a small-scale testing. Hopefully it will soon be more user-friendly and without dependency on the mobile app. When we get there, I will without a doubt push for implementing passkeys everywhere I go!!
Thank you for reading, I hope this was helpful. Remember that you can now subscribe to this blog so you will be notified as we publish new posts. Take care.
Discover more from Agder in the cloud
Subscribe to get the latest posts sent to your email.



[…] Update: A post with updated information can be found here. […]