The story so far
Just over a year ago (April 2024) we finally got the public preview of passkeys as authentication method in Entra ID. This was my most anticipated feature for 2024 and I eagerly awaited the opportunity to check it out, since this would be a very convenient way to transition users into passwordless and phishing resistant authentication. Perhaps in time even enabling a password-free workday.
The public preview was not without its limitations, and I wrote several posts on this blog where I discussed both its strength and weaknesses. One of my biggest frustrations was having to store the device-bound passkey within the mobile app, which imposed an unnecessary reliance on a mobile device and exactly the kind of dependency I was hoping passkeys would remove.
The end-user experience was also quite cumbersome in the start and Microsoft did some improvements, but at a big cost which I will come back to shortly. And in early 2025, device-bound passkey in Entra ID became generally available.
What is a Passkey?
Let us make sure we have a common understanding of passkeys. A passkey is a digital credential that’s entirely software-based, stored securely in a passkey-provider which can be on your device or your phone, and works seamlessly in the background to confirm your identity. This is a FIDO2-credential, but it is software-based and must be stored in a Passkey provider. In contrast, a FIDO2 key is dedicated hardware, like a USB stick that you have to carry with you. Passkeys simplify login by removing the need for a password and additional authentication steps, while still being very secure against phishing and hacking. This makes them a smoother, often more convenient solution than the traditional password-plus-MFA workflow or managing extra physical keys.
So how does it work as of May 2025?
In the tenant
Passkey in Entra ID is still not available by default, so you need to go in to Protection –> Authentication Methods, and click in to Passkey (FIDO2).
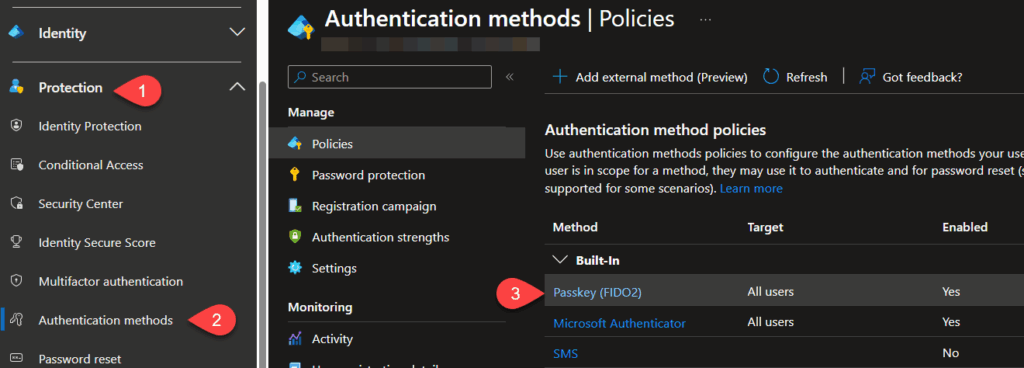
Enable the feature under Enable and Target and then select Configure. So a quick rundown from the top:
- Allow self-service set up must be enabled or end-users can’t set up any FIDO2 authentications on their own.
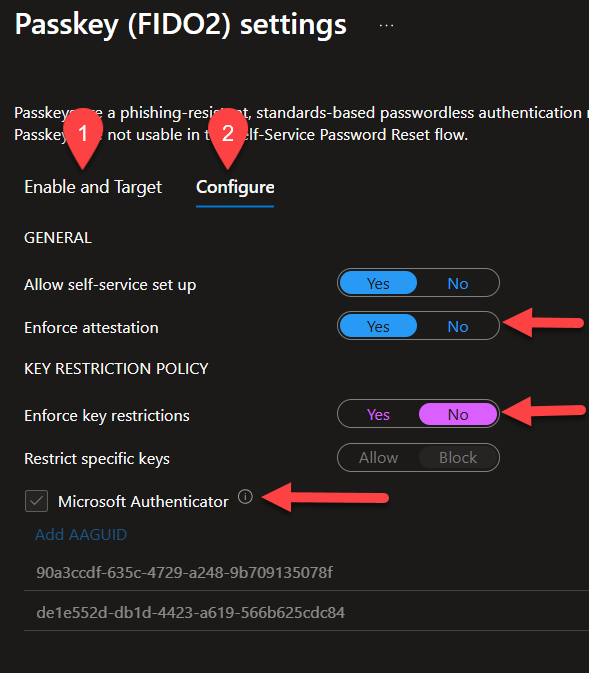
- Enforce attestation must be set to No to use the classic way to set up Passkeys, I’ll come back to this.
- Enforce key restrictions must be set to Yes before you can enable Microsoft Authenticator, but (and this part seems a bit odd to me) after you have enabled the Microsoft Authenticator checkbox, you can set Enforce Key restrictions back to No and it still works.😲🤔
For the end-user
Unfortunately this still has a lot of room for improvement in my opinion. There are currently 2 ways to register a passkey in the Microsoft Authenticator mobile app, and I assume this is because the original way during the open preview was very cumbersome and not user-friendly at all. So Microsoft added another method, so I’ll go through both ways to register a passkey. I’ll demo with a newly created user account with a Temporary Access Pass (TAP) for login and an Android mobile device. Also beware that Bluetooth connection is required.
Method 1: Register a “separate” passkey in the mobile app.
Note: Enforce attestation must be set to “No” for this method to work.
This was the original way to register a passkey and I don’t think Microsoft wants you to use this method because it is hidden away quite well for the end-user.
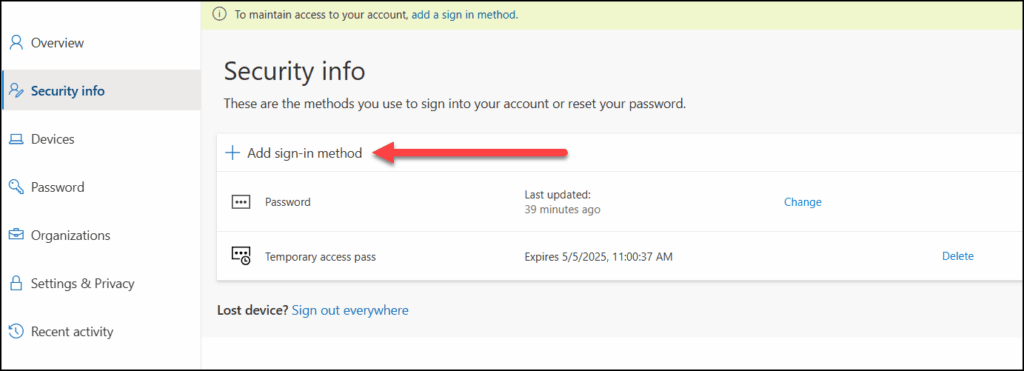
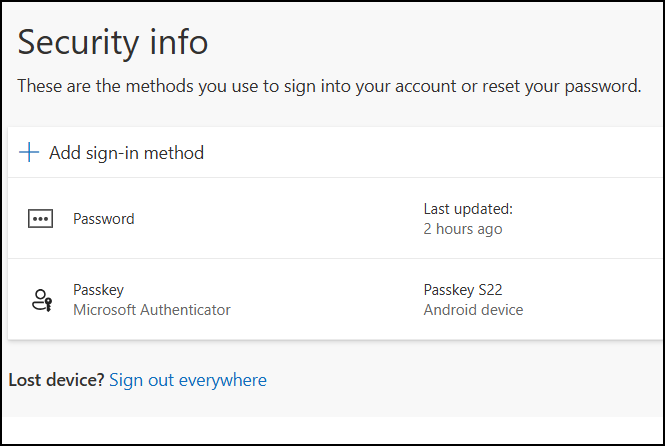
1. Here I have logged in to https://aka.ms/mysecurityinfo with my newly created user using a TAP to mimic a password-free solution. So to add a passkey I must select Add sign-in method.
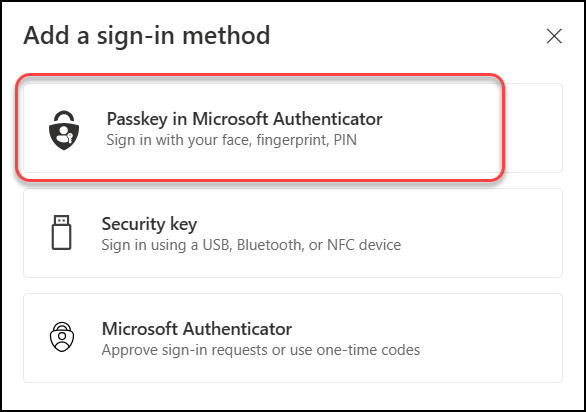
2. Select Passkey in Microsoft Authenticator.
3. Immediately on the popup, select Having trouble? which will allow you to click on the link saying Create your passkey a different way.
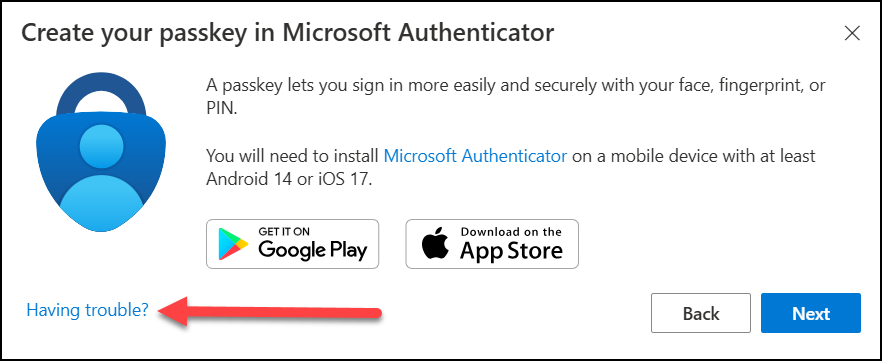
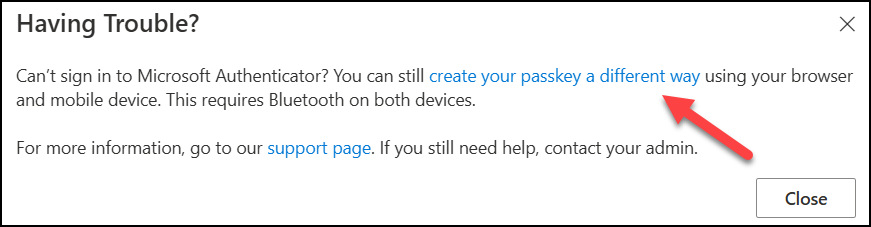
4. This opens up a new wizard
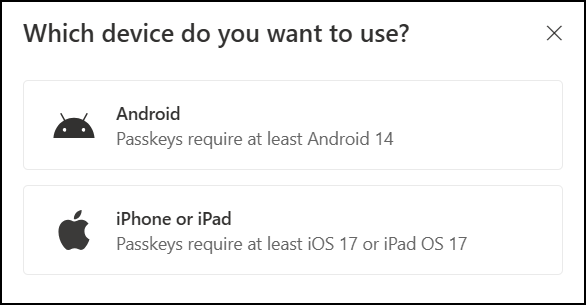
- Select Android or iOS
- Also make sure Bluetooth is enabled on both devices (the phone and your computer)
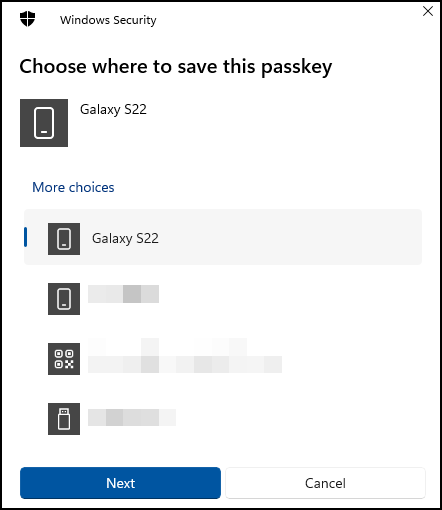
- Select which device to connect to with bluetooth (to confirm it is a local device)
- This list of saved devices is stored in the registry. So if you want to remove devices from this list open regedit and navigate to
Computer\HKEY_USERS\S-1-5-20\Software\Microsoft\Cryptography\FIDO\%your SID%\LinkedDevices
5. On the mobile device: Make sure that Microsoft Authenticator is set as provider for the passkey! On the pictures below you see that Samsung Pass is suggested as provider so this must be changed on the passkey registration will fail.
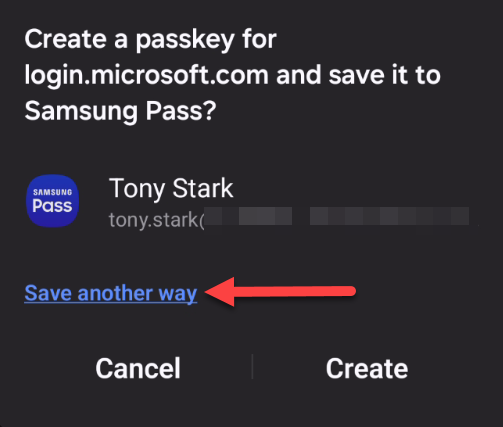
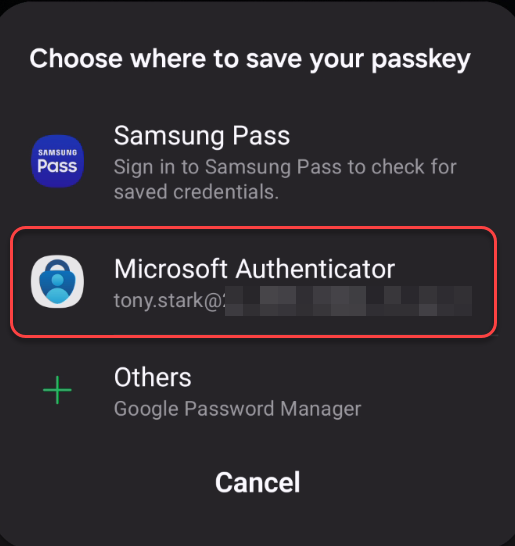
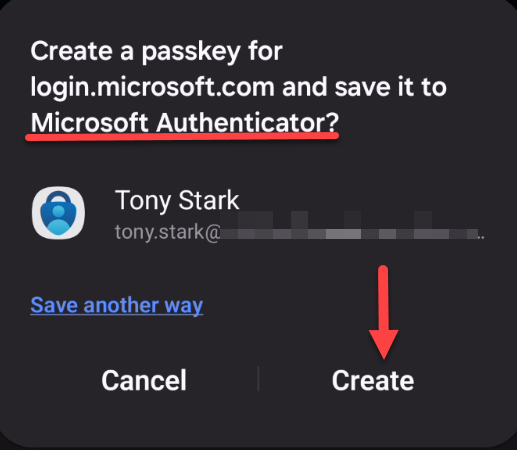
6. Verify that “Microsoft Authenticator” is selected and tap “Create“.
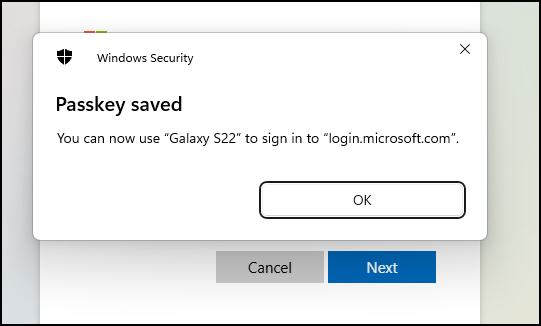
7. On the computer: You will see the confirmation hat the passkey is saved and you are asked to give it a displayname and then it is ready for use.
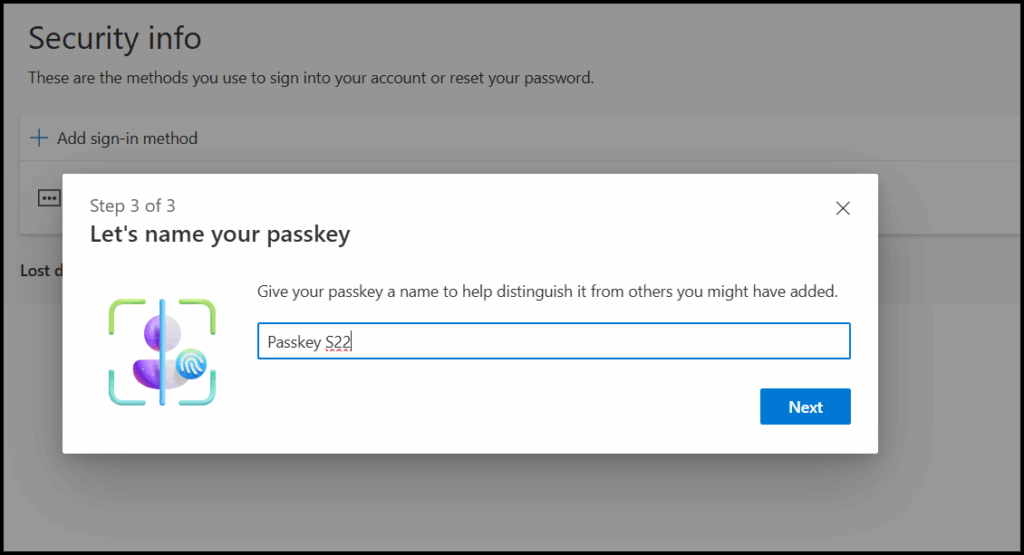
Method 2a: Sign in to the mobile app – existing user
As mentioned the method above is very cumbersome for end-users and so last winter, Microsoft launched an alternative method which involves that you sign in to the Microsoft Authenticator mobile app using your work account. Also, beware that multiple accounts can be signed in at the same time in the same mobile app.
The steps here vary slightly depending on your starting point, as is if you’re an existing user or a brand new user being onboarded into the tenant.
1. On the mobile device, just open up the Microsoft Authenticator app and locate your account there.
In this scenario the user is already using MFA with push notifications in the Authenticator, so the screen will look something like this.
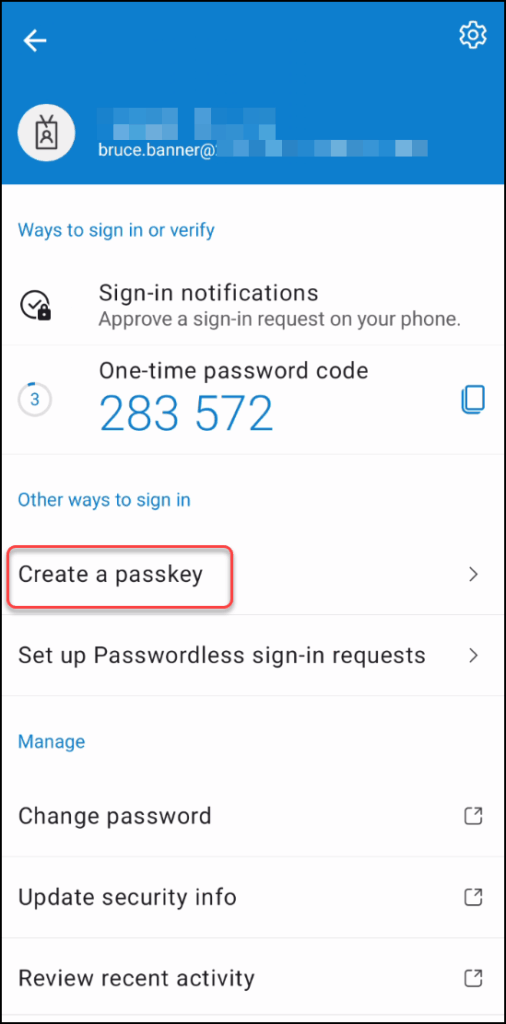
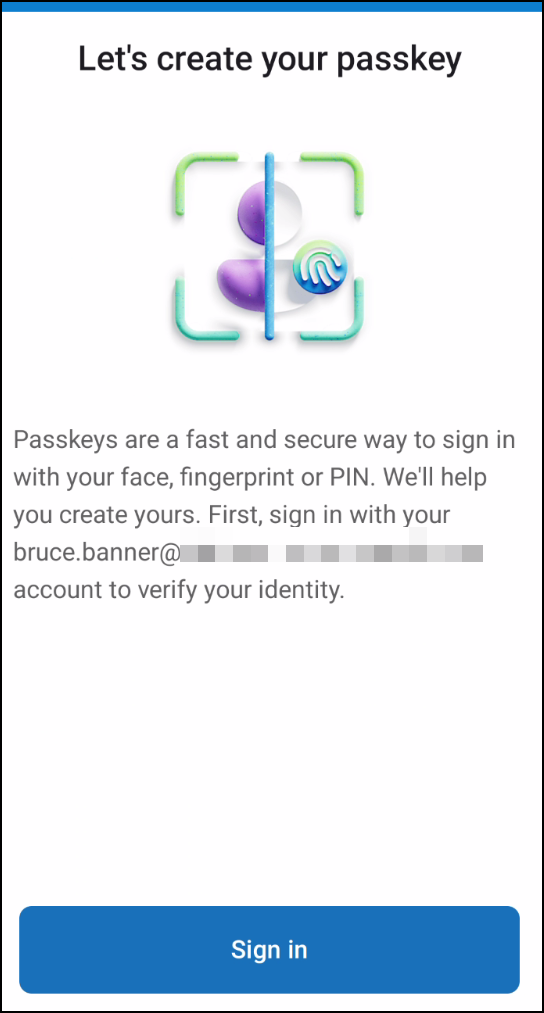
Here you can tap Create a passkey and the user will be prompted to log in with his/her account
2. The user is prompted to sign in:
3. Make sure Authenticator app is enabled as a passkey provider.
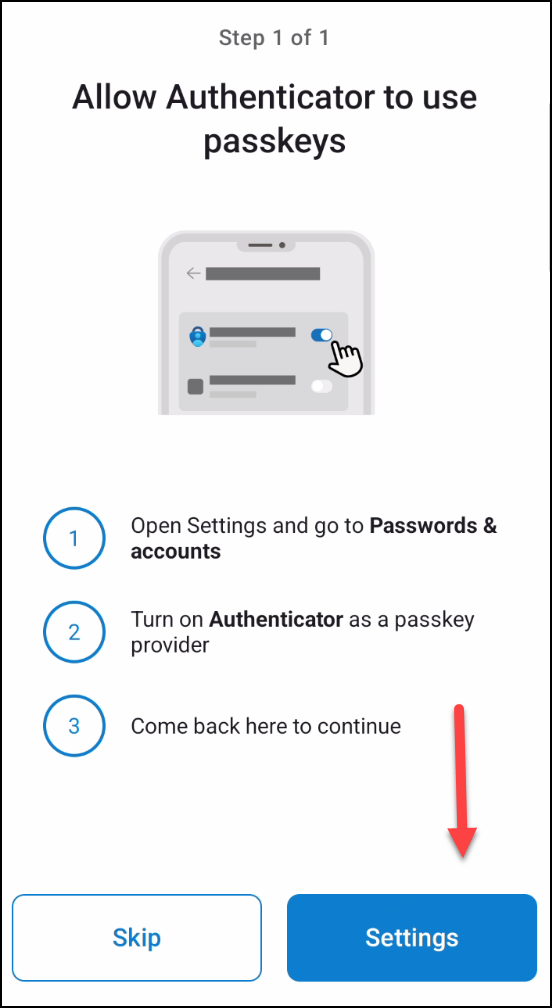
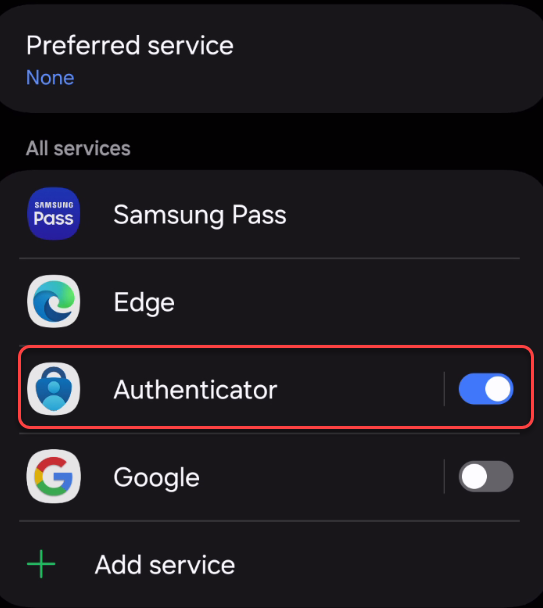
4. Now the passkey is created and the phone will perform a local, biometric authentication: Fingerprint or facescan, depending on your device and configuration.
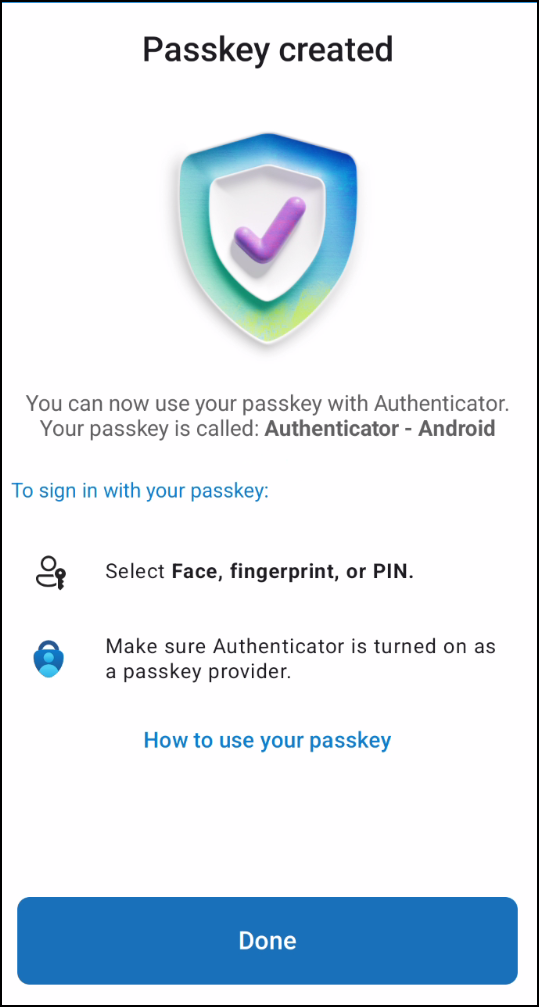
Method 2b: Sign in to the mobile app – New user
In this scenario you can actually set up MFA and passkey directly in the mobile app first, before logging in to your computer at all.
1. Create the user account in Entra ID and assign a TAP
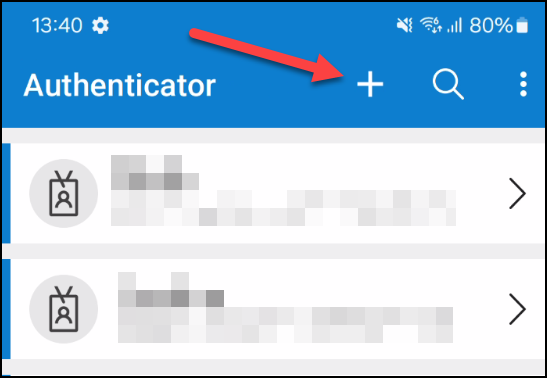
2. The end-user opens the Microsoft Authenticator app on the phone and adds a new account by tapping the plus-sign on the top and, select work or school account and sign in.
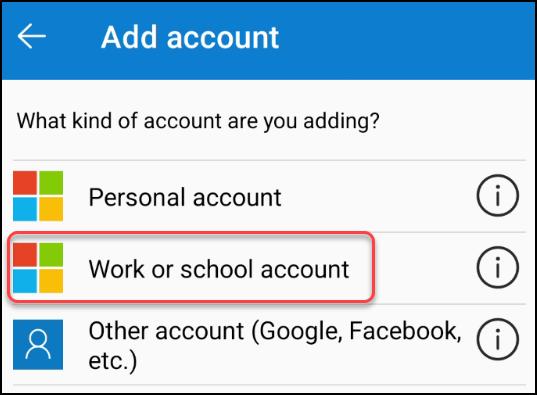
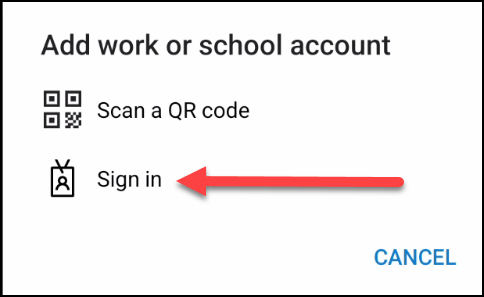
3. Enter username and TAP to sign in
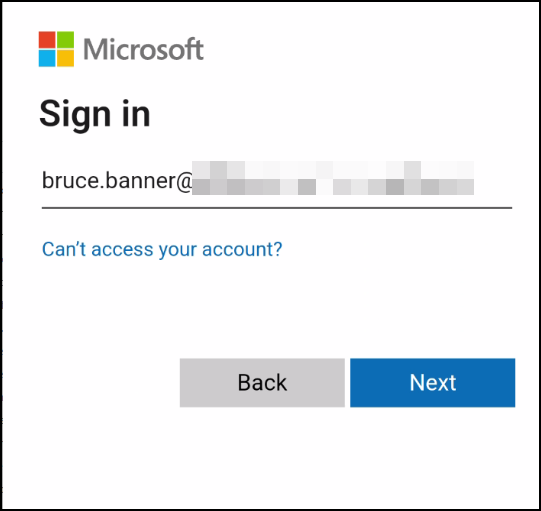
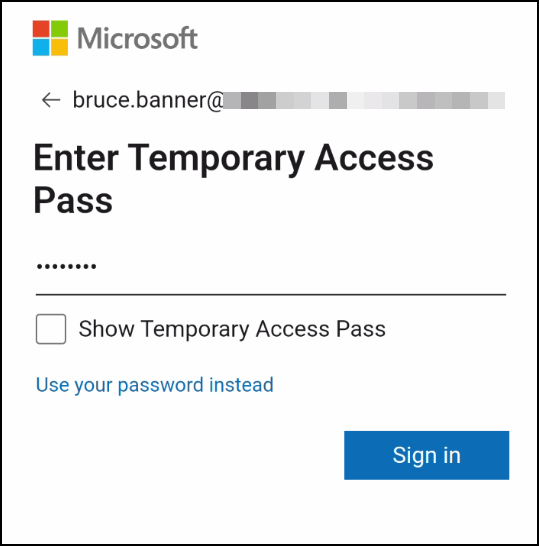
4. The app will then automatically configure your MFA methods for you, and which methods it configures will depend on the configuration in your tenant. For example, if “Passwordless sign-in” with Authenticator app is disabled in the tenant, that method will not be configured in the app.
So these are my thoughts about Passkeys for Entra ID
Regarding the tenant configuration:
The settings in the tenant has remained almost identical for the last year. There’s still an issue that passkeys are an “all-or-nothing” setting since it is a setting within the Passkey (FIDO2) method. Meaning that you can not enable Passkey in authenticator app for only one set of users, and other FIDO2 methods for another set of users at the same time. Personally I would love an option to enforce only physical FIDO2 keys for a group of users, privileged users for example.
Regarding user experience in method 1:
This method is very cumbersome to set up and I completely understand why people would not appreciate trying to enroll passkeys on a few thousand users with this method. It only advantage is that it does not require a sign-in on the mobile app like method 2 does.
Regarding user experience in method 2:
This method is more streamlined and easier than the first method, and I can definitely see the appeal by signing into the authenticator app, and let it automatically set up all available authentication methods for you. This feature is actually really cool and helpful, especially for new user accounts (Method 2b).
❗However, method 2 is to me a complete no-go for protecting privileged accounts. I can not see myself approving that accounts with privileged access (even if it is with PIM) sign in to an app on a mobile device. I would strongly argue that those accounts should only sign in from secure, dedicated PAWs (Privileged Access Workstation). So for these accounts I’m leaning towards physical FIDO2 keys as the only suitable MFA method.
Passkeys – what is missing?

The good part is that Passkey in Microsoft Authenticator has been steadily improving since the preview began last year and it now works very, very well once it is set up. It is a strong, phishing-resistant and password-free authentication method. This makes it much more secure than the traditional password+MFA method, and at the same time the user experience is much better (again, after it has been set up). It IS a very easy and safe way to authenticate despite my next paragraph…
But there’s that dependency I’ve talked about…😞
Unfortunately, my biggest critique for Passkey in Microsoft Authenticator is still the same: The imposed dependency on the mobile app is one of the biggest showstoppers and there are several usergroups who can’t reliably access a mobile phone! The most prominent example is still students of all ages, not only kids who doesn’t own smartphones, but more and more schools want mobile-free classrooms. Other examples are healthcare and factory workers and for these groups of users. For these usergroups, MFA is already a HUGE challenge! Passkey has a great potential to solve this major challenge if we would be able to use passkey providers integrated in the local device itself.
Luckily, Microsoft is still working on Passkeys so I am cautiously optimistic that these issues will be addressed, and I have absolutely no doubt that the passkey adoption will accelerate greatly in the coming years. Microsoft has previously announced that sync-able passkeys are coming, and this will hopefully include support for local passkey providers (meaning no more mobile app dependency). Passkeys, and physical FIDO2 keys, offer a more secure solution which also is easier and faster to use.
Who would prefer to mess around with complex passwords instead of this?
Discover more from Agder in the cloud
Subscribe to get the latest posts sent to your email.


