What is a “Workload Identity” anyway?
So let’s start with the beginning. A “Workload identity” is for all intents and purposes a more modern alternative for traditional service accounts. While a traditional service account has historically been non-personal accounts that rely on passwords, a Workload Identity is a modern alternative to the traditional service account, which previously required static passwords and manual management. Unlike service accounts (which can be compromised through brute-force attacks or credential leaks) Workload Identities rely on authentication methods such as certificates, tokens, and managed identities. These mechanisms provide stronger security because they eliminate password-related vulnerabilities and enable seamless, automated authentication.
| User accounts | Workloads |
|---|---|
| Traditional user accounts. Used by and associated with normal people | A non-human identity that an application, service, script, or container uses to authenticate and access resources. |
| Authenticate normally with passwords+MFA or biometrics. | Authenticate normally with secrets, certificates, or federated tokens. No traditional passwords |
| Used by real people to access resources the person needs. Like employees, administrators, customers etc | Used by machine-to-machine communication. Like APIs, automated workflows, etc |
| Compromised by phishing or stolen passwords | Can’t be phished, but susceptible to misconfiguration or stolen tokens/certificates. |
The challenges with Entra Workload ID
What you may not know is that in Entra we have 2 tiers of Workload ID: Free and Premium! The free tier is automatically available in your tenant. You have very likely already started using Workload IDs, since this includes Service Principals, which is automatically created when you create an enterprise application or application registration in your tenant. The Free tier let’s you do the basic things like creating/changing/deleting Workload IDs, and use them to access resources. But that’s pretty much it, you can set it up and then it kind of just stays “over there” and takes care of itself. Sure, you can check sign-in logs and manipulate the authentication methods (depending in the app of course) but there’s really no good way to monitor and secure those identities.
Entra Workload ID Premium
💡 So this is where the premium tier shines! It unlocks some additional and very powerful features (Link) which let you monitor and control Workload IDs almost as well as ordinary user accounts. It enables:
- App health recommendations
- Access Review for service principals with privileged roles assigned
- Entra ID Protection – service principal risk
- Conditional Access policies
Workload ID Premium is a separate license, is currently not included in any bundles, and must be purchased separately for $3/workload identity/month. A 90-day free trial is available.
Workload ID App Health Recommendations
This is a feature you may have seen already. In your Entra admin portal you will see a list of recommendations, located under “Overview” and then “Recommendations“.
With Workload ID licenses, your workload identities are included in the list which will help you identify inactive and potentially compromised or expiring/expired credentials.
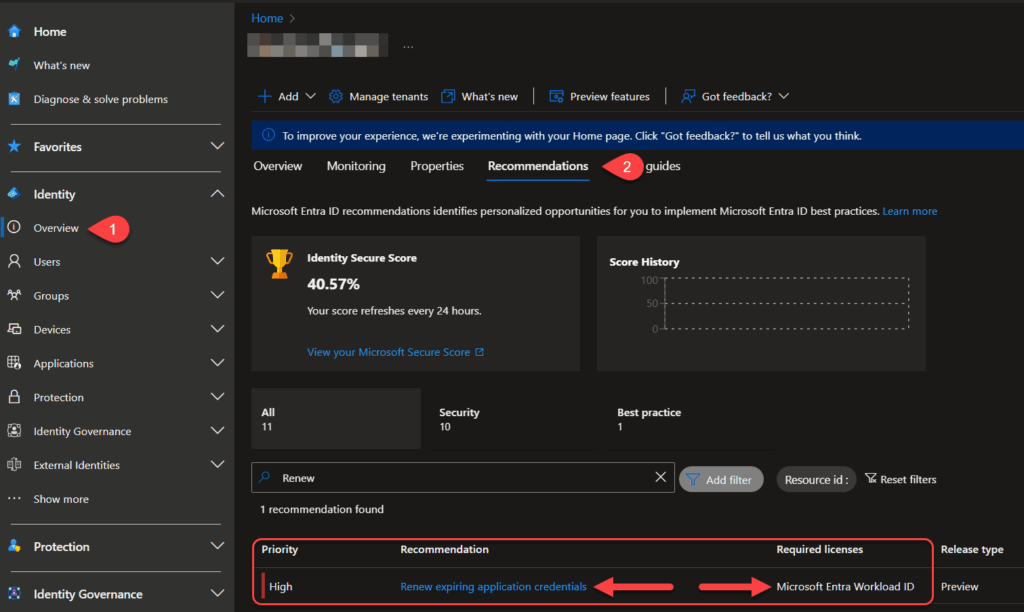
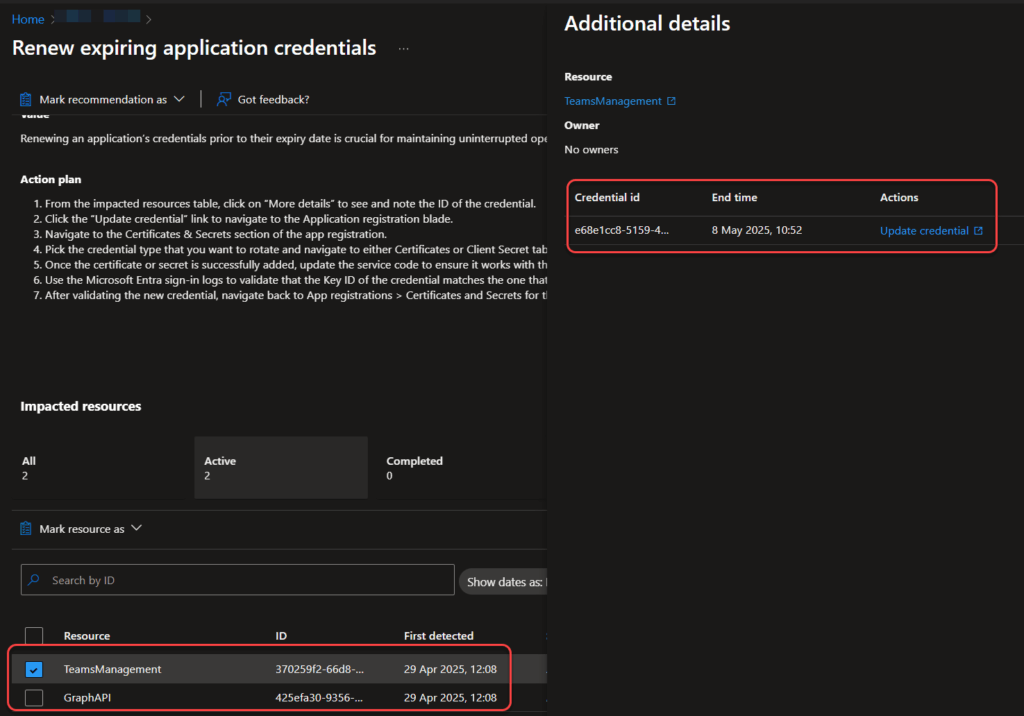
Clicking on the recommendation, I get a list of 2 apps with credentials about to expire.
Access Review for privileged roles assigned
An access review for Workload ID means regularly examining privileged role assignments to workload identities. This process ensures that each identity holds only the permissions required to perform its functions. By adhering to the principle of least privilege, you significantly reduce the risk of over-privileging and potential security breaches.
This setting is slightly hidden. You can’t, as far as I know, find it under “Access Reviews”. You must navigate to “Identity Governance“, “Privileged Identity Management” and select “Microsoft Entra roles“.
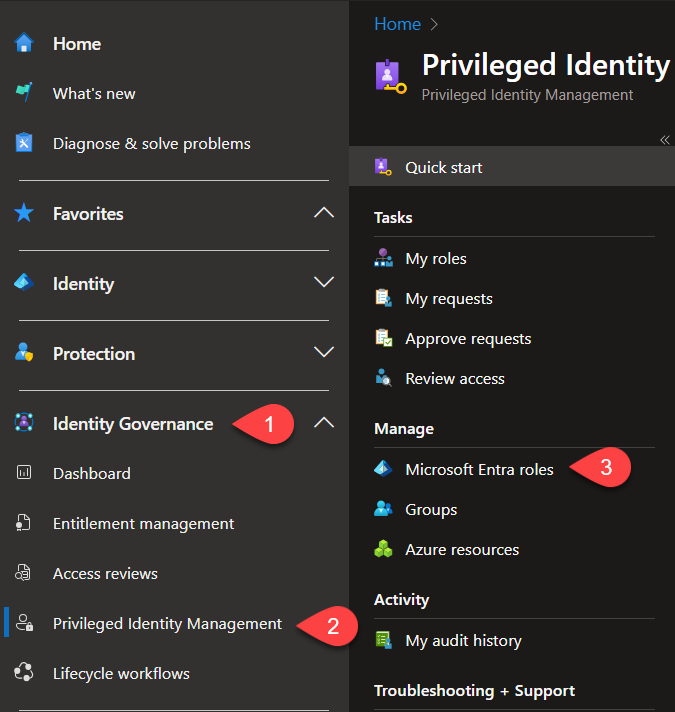
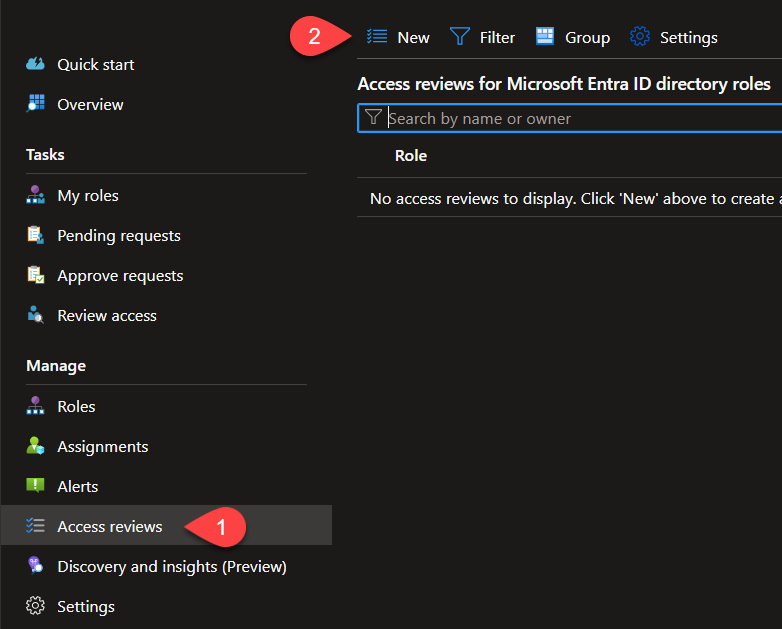
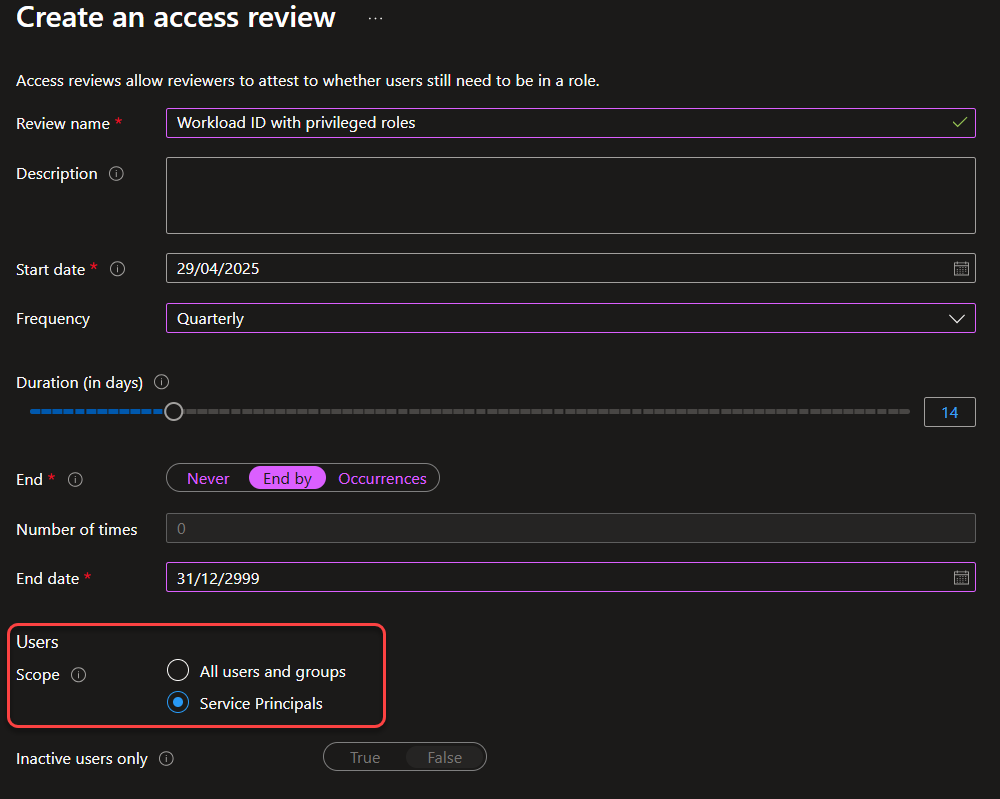
Now select “Access reviews” and “New” to create a new access review.
On the new screen, you can choose “Service Principals” as your review scope. If your tenant doesn’t have any Entra Workload ID licenses, this option will appear greyed out.
Entra ID Protection – service principal risk
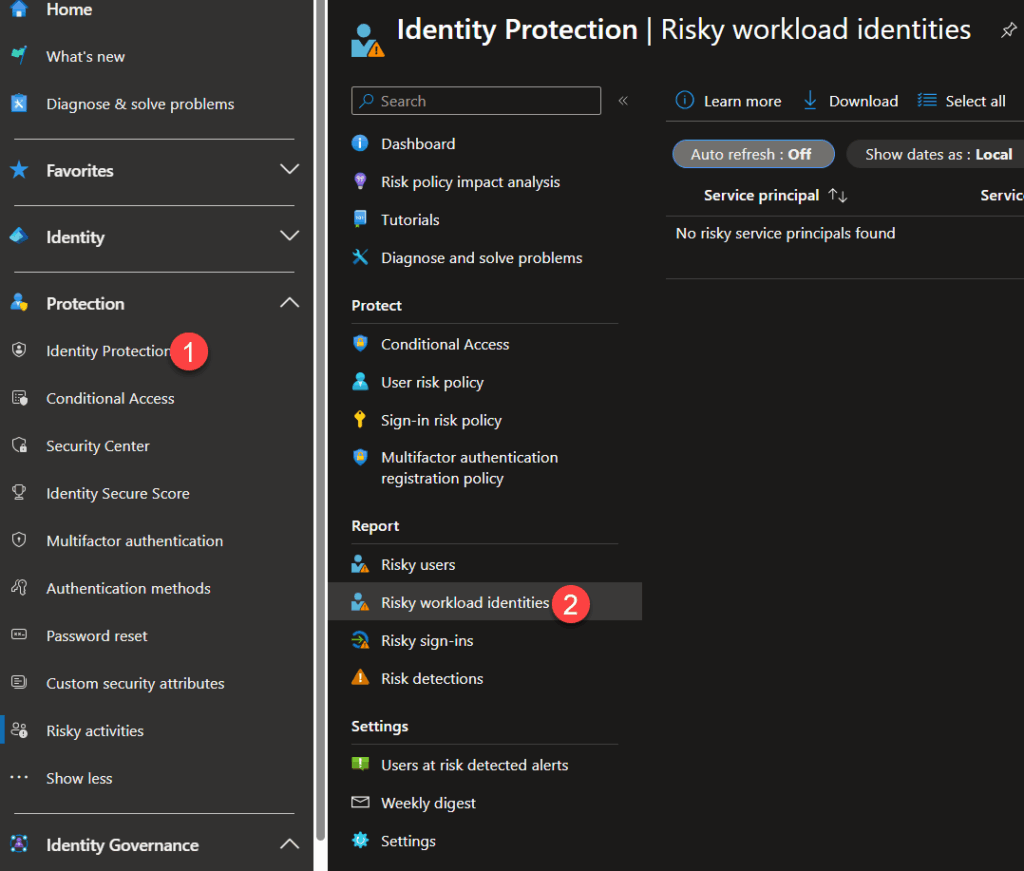
This one is pretty straightforward. Just like user risk, Entra will monitor your service principals and flag them with a risk assessment based on their behavior. The risk detections are available in the Entra admin portal under “Identity protection” and “Risky workload identities“. The free tier does include risk detection but with limited reporting details. The preferred way to respond is setting up risk-based Conditional Access policies, which will require the Workload ID licenses. More information here.
Workload ID with Conditional Access
For those of you who know me, you already know how much I appreciate Conditional Access, so not surprisingly this feature is my favorite. While it does follow the same structure as ordinary Conditional Access, there are some very important differences here. So here’s quick tour:
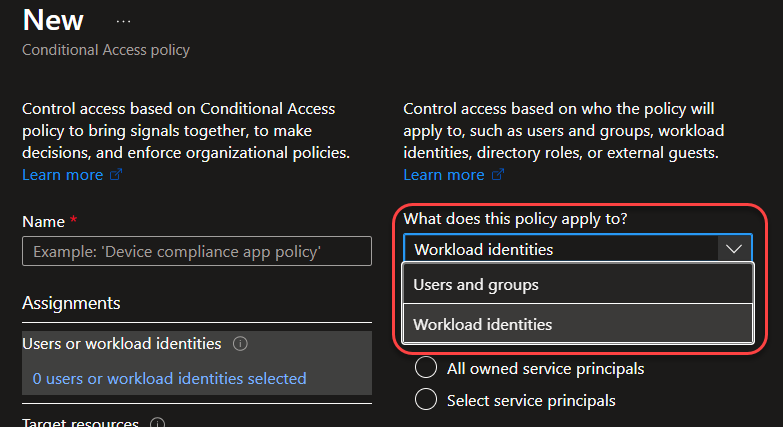
The UI in Conditional Access changes slightly when you add Entra Workload ID licenses to the tenant. When you create a new policy the top choice is renamed from “Users” to “Users or workload identities” and you now have a drop-down menu to scope the policy to either one. Beware that Conditional Access can for now only be applied to single tenant service principals owned by your organization.
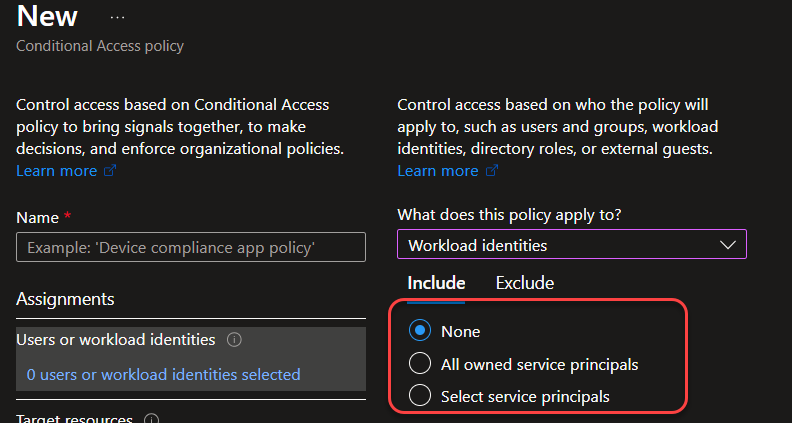
I’m selecting “All owned service principals” and move on to “Target resources“. Where I can choose either “Resources (cloud apps)” or “Authentication context“. Individual cloud apps can’t be selected, unfortunately.
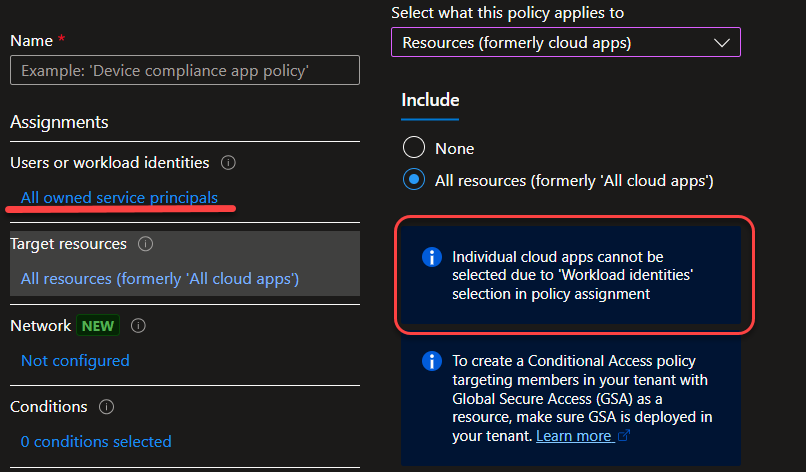
Moving on to “Conditions” we see the biggest difference from traditional Conditional Access policies. We are very limited in our options and can only filter on
- “Service principal risk” (Low/Medium/High, works in the same way as User Risk)
- “Locations” (IP/Country filter)
I really wish we had at least device filter as an option here, because it is a very flexible and powerful feature! You should take a look here!
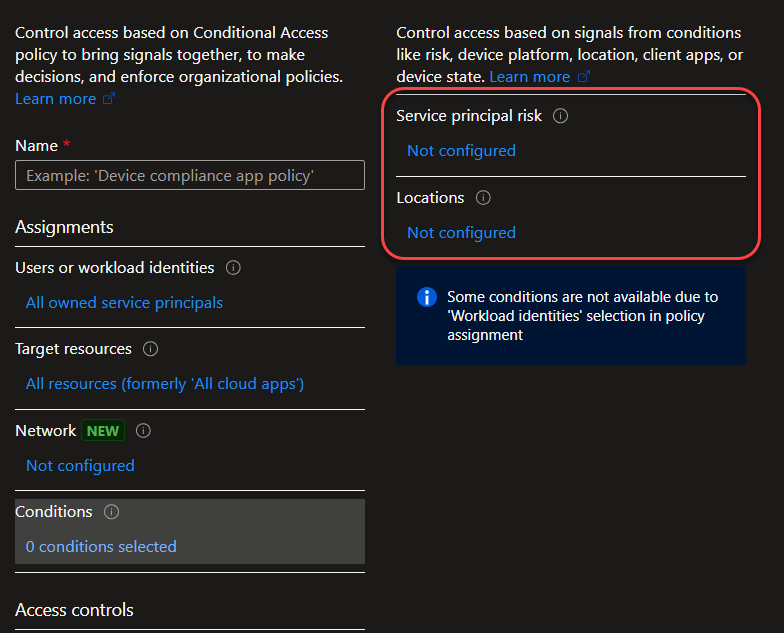
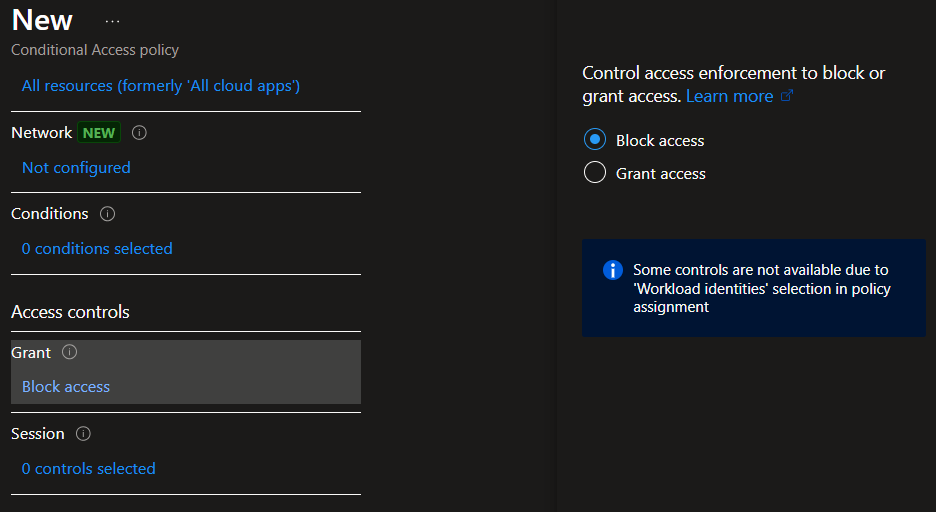
Moving on to “Grant“, there isn’t much to choose from, it’s either block access or allow access.
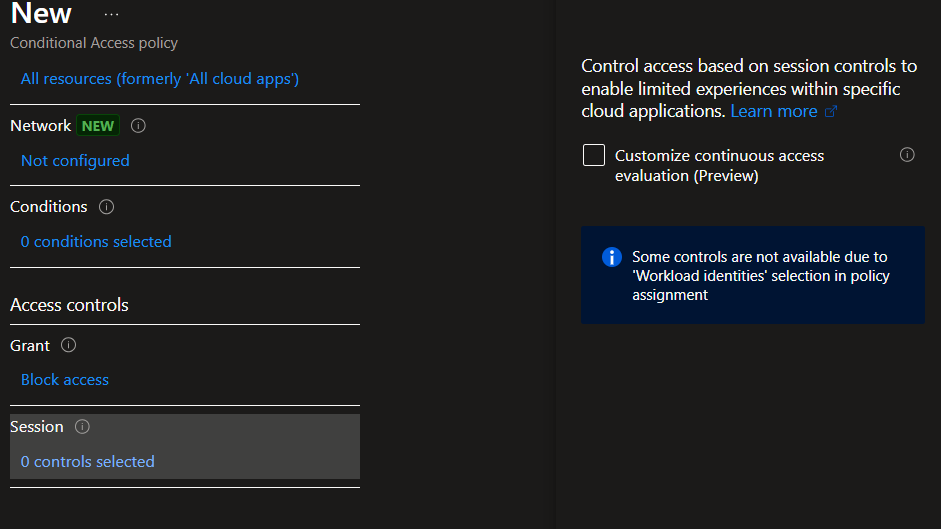
And finally there’s “Session” with only 1 option: Toggling CAE (Continuous Access Evaluation).
So as I just showed, Conditional Access policies can be applied to secure workload identities, providing a big leap forward in protecting these non-human accounts. However, when compared to the robust and granular options available for traditional user accounts, the customization here remains quite limited.
Currently, the filtering capabilities are restricted to criteria such as geographic locations (via IP or country filters) and service principal risk levels. While these checks help, they only offer a high-level safeguard and don’t address the full range of factors that modern security environments require.
In my opinion, the biggest downside is the lack of a device filter. 😱 In today’s zero-trust landscape, ensuring that the device accessing your resources meets strict security and compliance standards is critical. A device filter would enable administrators to enforce policies for workloads based on endpoint health, ensuring that only dedicated devices with up-to-date security patches, compliant operating systems, or approved configurations are allowed access using your service principals. While the existing Conditional Access mechanisms for workload identities offer a better alternative than having no controls at all, the absence of device-based filtering is a missed opportunity which I really hope Microsoft will address soon.
Conclusion
So to summarize, Entra Workload Identities are a modern, secure way to handle non-human identities. The free (and default) version covers the basics, while the premium tier unlocks helpful features like app health recommendations, access reviews, and conditional access policies. These tools help keep your automated services safe (even if there’s still room to add options like a device filter). Overall, Entra Workload ID is definitely worth a closer look since it allows you to secure your service principals, which often possess privileged access into your cloud environment, and securing these accounts is an important part of your security posture!
Discover more from Agder in the cloud
Subscribe to get the latest posts sent to your email.


