Happy new year and welcome to 2025! 🥳
In today’s fast-paced digital landscape, staying informed about critical activities within your tenant is essential for maintaining security and efficiency. One way your tenant admins can stay informed is through various email notifications. However, setting up these notifications can be more complex than it seems. Challenges arise because privileged accounts should not be licensed for M365 services like Exchange Online, which can prevent notifications from being received.
Additionally, ambiguous terms like “admin” can lead to confusion, as different roles and permissions might be referred to by the same term. This can make it difficult to ensure that the right individuals are receiving the necessary updates. Properly configuring these notifications requires careful attention to account permissions and clear communication about roles and responsibilities.
The challenges with email notifications in Entra
Challenge #1: Just who is “Admin” ?
This part is slightly different depending on where you are in Entra, but I will use PIM/RBAC as an example as it is one of the most prominent one. Below you see the notification settings when assigning a role to a user, and you have the option to send “Admin” an email notification if anyone is assigned eligible to this role. Nowhere does it say which account(s) is/are considered as “Admin” in this context.
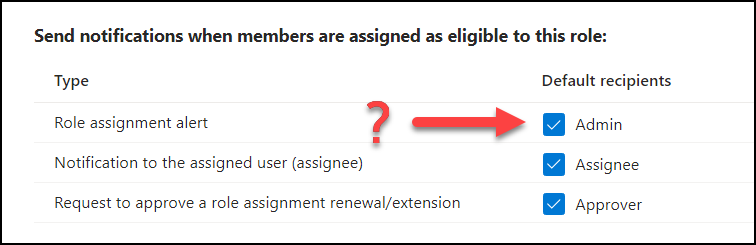
So this means you need to find out which roles will receive notifications as “Admin” but to make matters more complicated, these roles can vary depending on which service in Entra you’re looking at. For example: The role “Privileged Role Administrator” will receive email notification from PIM/RBAC, but will not receive notification from Entra Identity Protection when a user is flagged as risky.
Confused yet? Yeah, me too. 😉
In short, the roles that receive email notifications vary depending on the specific Entra service. However, I think it’s safe to assume that Global admins will always be included.
Challenge #2: Email requires licenses, but we don’t want to license our privileged accounts
In order to receive emails in M365, a user must be assigned a license for Exchange Online. However, it’s highly recommended not to assign licenses to admin accounts. Here’s why:
Admin accounts should not use services like Exchange, SharePoint, or Teams because doing so increases the attack surface of these accounts. This makes them more vulnerable to potential security threats. Instead, IT personnel should have at least two accounts:
- Admin Account: This account should be used solely for administrative tasks and can elevate to higher roles using Privileged Identity Management (PIM). If you have tiered admin accounts, you may have more than one of these. These accounts should also have stricter requirements for signing in like phishing resistant MFA methods and client restrictions.
- Ordinary Work Account: This account has access to email, Teams, and other daily work services.
Challenge #3. Emails are only sent to active role members
When an event triggers an email notification, the notifications are sent only to those admin accounts that are active members of the required role at the time the notification is triggered. Accounts who are eligible, but not active, will not receive email notifications. Taking this point a step further: In my mind a “perfect scenario” is that every single admin in your tenant are only eligible for their roles (and for a limited time) and only activate these roles using PIM when needed. This means that in this scenario: The only account in your tenant with permanent and active membership to the Global Administrator role is your break-glass account.
Considering the three challenges I’ve mentioned, my recommendation is to rely on break-glass account(s) for email notifications for admins, since this is potentially the only account which will receive all notifications. But additionally, it’s important to monitor email notifications sent to your personal admin accounts, as these may include important account-specific alerts, such as requests to approve extensions of other role delegations.
Introducing: + addressing in Exchange Online

Exchange Online has a hidden gem which is called “plus addressing“, and this is enabled by default. Plus addressing lets your create unique and disposable email addresses by adding a tag in an existing email address, identified by a plus sign (+). This new address is receive-only and is not supported by on-premises Exchange Server.
You can add this feature to any existing email address in your tenant. Here in my Game of Thrones inspired demo environment, I simply add a “+” and any desired text (known as a tag) just before the “@” symbol in the email address.
For example:
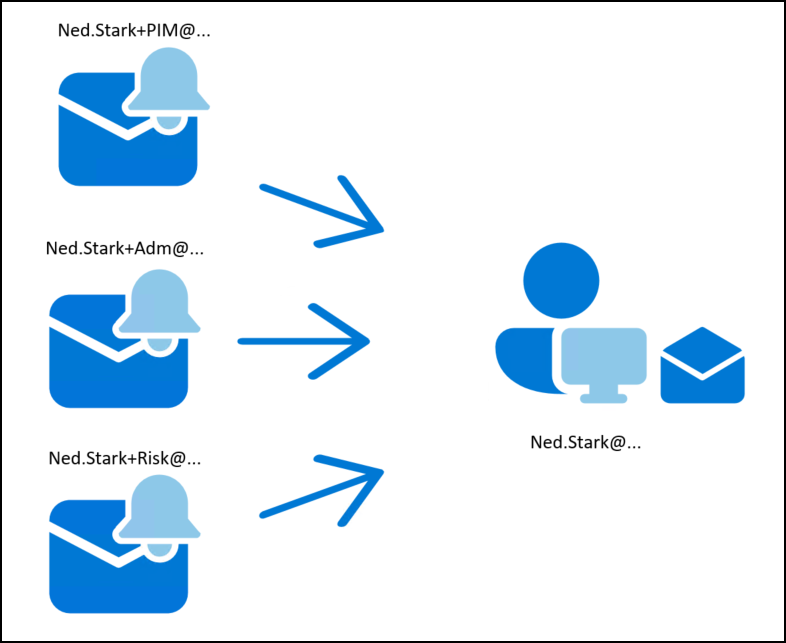
- “Ned.Stark+Adm@…” will automatically deliver emails to “Ned.Stark@…” which belongs to the ordinary account mentioned earlier.
- You can create multiple plus addresses for the same mailbox, such as “Ned.Stark+PIM@…” and “Ned.Stark+Risk@…”. All these emails will be delivered to the same mailbox (Ned.Stark@…), allowing you to easily organize incoming messages using mailbox rules.
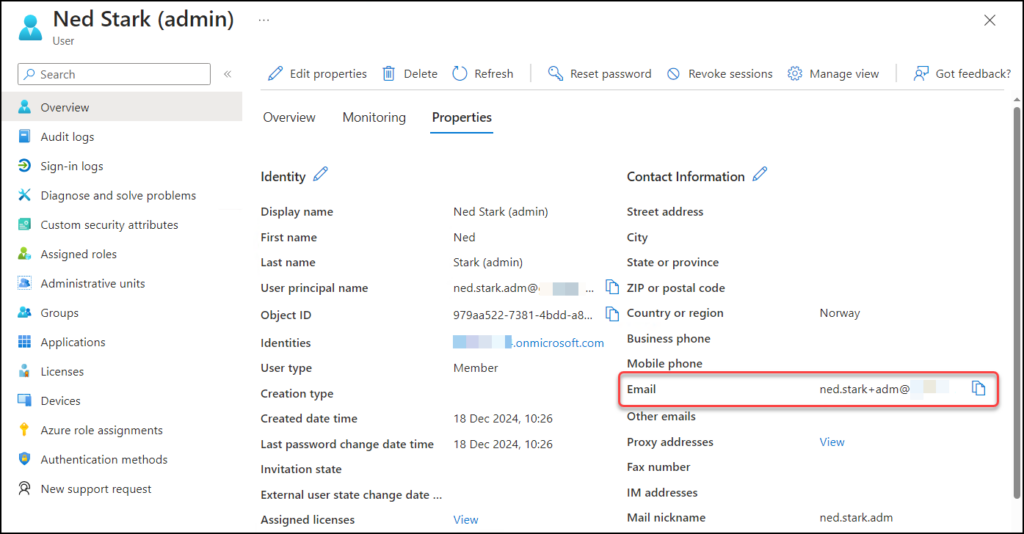
Using plus addressing for admin email notifications:
Below you see Neds unlicensed admin-account has a plus address (“ned.stark+adm@…”) set in its E-mail field, and that’s all you need to do! 🥳
Please note that notifications sent to this account will only use the “Email” field, so only one mailbox will receive any notification email. You can’t enter multiple email addresses. This means that you may want to consider sending email notification targeted to your break-glass account, to a shared mailbox or other non-personal recipient.
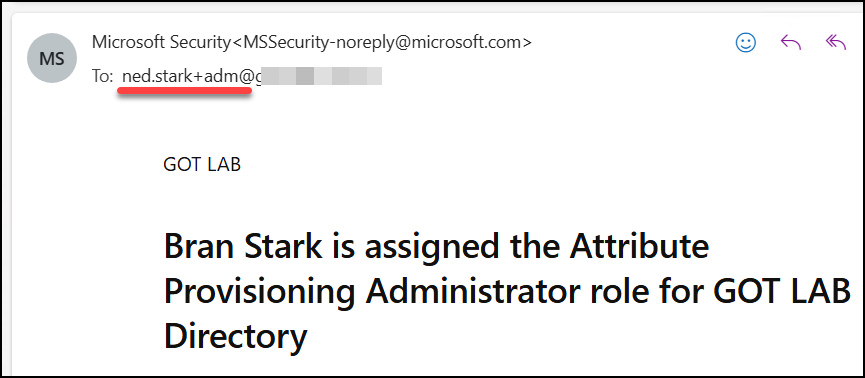
When an email notification is triggered, by a role delegation in this example, the email is delivered to the inbox of Ned Starks ordinary user account with the plus addressing visible.
✅One of the major benefits with plus addressing is that this method does not require any further configuration so it is extremely easy to get started. Just add an address and you’re done!
❌Unfortunately, plus addressing is not compatible with all email services, including on-premises Exchange Servers. This incompatibility means that in an Exchange hybrid scenario, where mail is routed through on-premises servers, external emails sent to a plus address will not be received. Additionally, if your email passes through any third-party filtering services that do not support plus addressing, those emails will also not be received. Therefore, it is crucial to check the compatibility of plus addressing with all components of your email infrastructure to ensure proper email delivery.
The alternative: Using transport rules
If you can’t use plus addressing for one reason or another, you can use contacts and transport rules in Exchange online to achieve much of the same functionality. However, this method requires more effort to set up.
In this example I use the admin-account for Sansa Stark. Her admin-account is of course not licensed and this account has no email addresses registered.
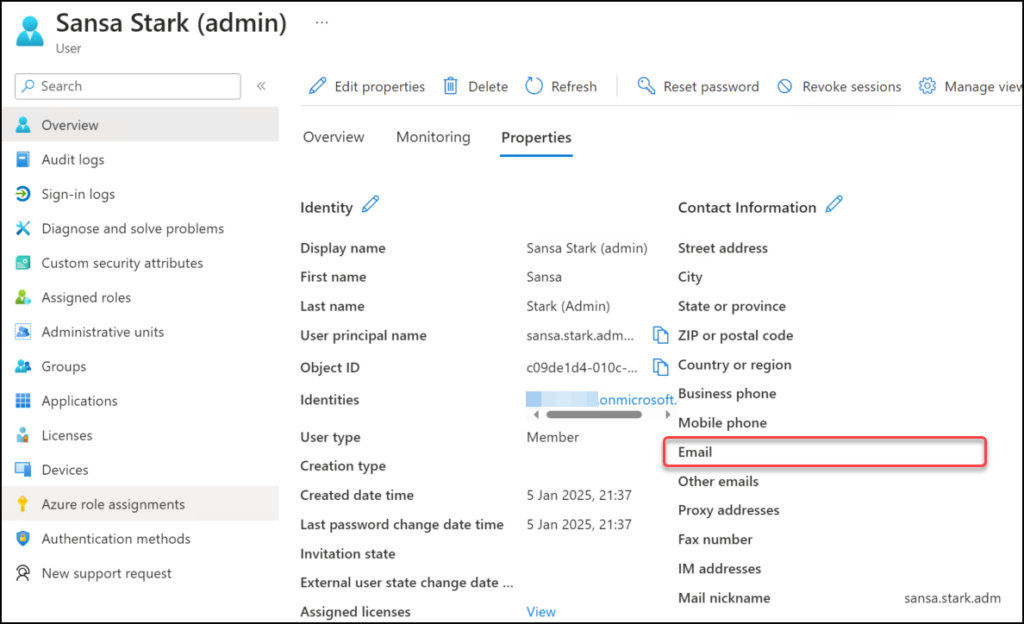
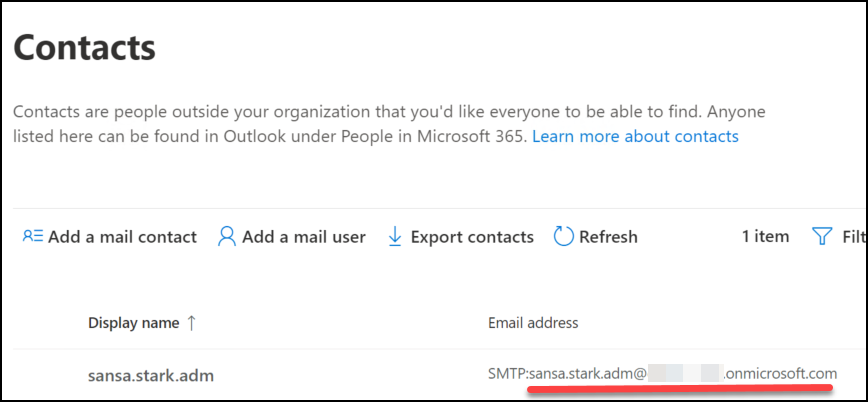
In Exchange Online: Navigate to “Recipients” and “Contacts” and create a new mail contact with email address matching the UPN of the admin account in question.
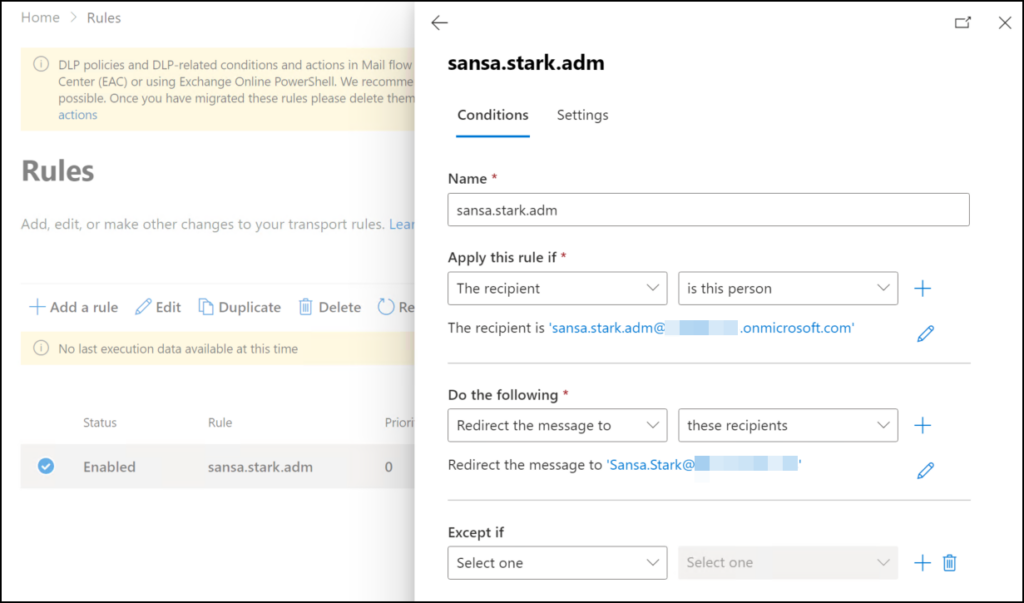
Once the contact is created in Exchange Online, navigate to “Mail flow” and then “Rules”. Create a rule to forward all mail sent to the contact to the user’s regular mailbox. Don’t forget to:
- Enable the rule after creating it, as rules are disabled by default.
- Do audits/monitoring so these rules are not modified to send alerts to unauthorized recipients
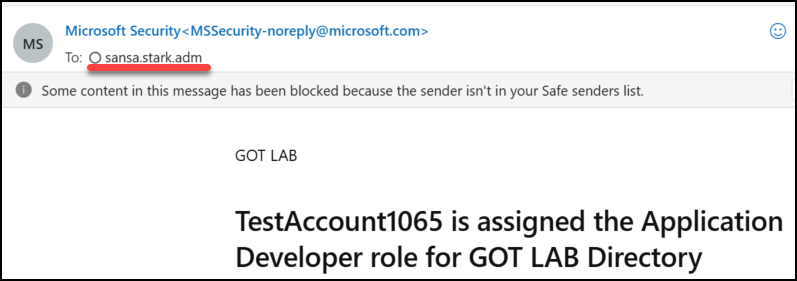
And a quick test shows that admin email notifications are delivered to Sansas mailbox.
But, do we really need these emails?
I know some of you might be thinking, “Hey! The 2000s called and they want their communication method back!” 😂 While email isn’t the most modern or innovative way to communicate, it can still be useful for catching important information. Most email triggers can be found in audit or sign-in logs and can alternatively activate alerts through log analytics, logic apps, scripts, SIEM solutions, etc etc. So, perhaps it’s more efficient for you to use these methods? Other features, like reports or digests, aren’t triggered by specific events but usually summarize events over a certain period and are sent out on a schedule. So whether these emails are useful or not is really up to you, and it’s not something I can tell.
Conclusion
Configuring email notifications in Entra ID can be tricky, especially with unlicensed admin accounts and confusing terms. However, with features like plus addressing in Exchange Online, alternatively using contacts with transport rules, you can help ensure important information reaches the right people.
While email may seem outdated, it remains a valuable tool for catching critical information. Ultimately, the choice of method depends on your specific needs and infrastructure compatibility.
Thank you so much for reading! Stay informed, stay secure, and here’s to more knowledge sharing in 2025!
Discover more from Agder in the cloud
Subscribe to get the latest posts sent to your email.


