(This is a follow up on my earlier post: Microsoft-managed Conditional Access policies!)
First look: Microsoft-managed Conditional Access policies
Today in one my customers tenant I found 2 new CA policies, tagged as “Microsoft-managed”.
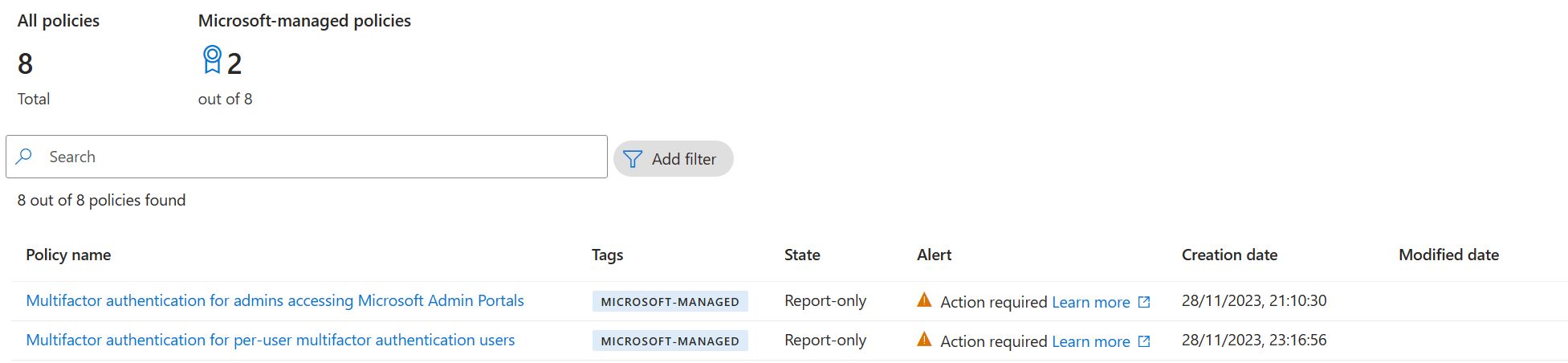
These CA policies are a little different from ordinary CA policies. If you click into one of them, you get a slightly different overview:
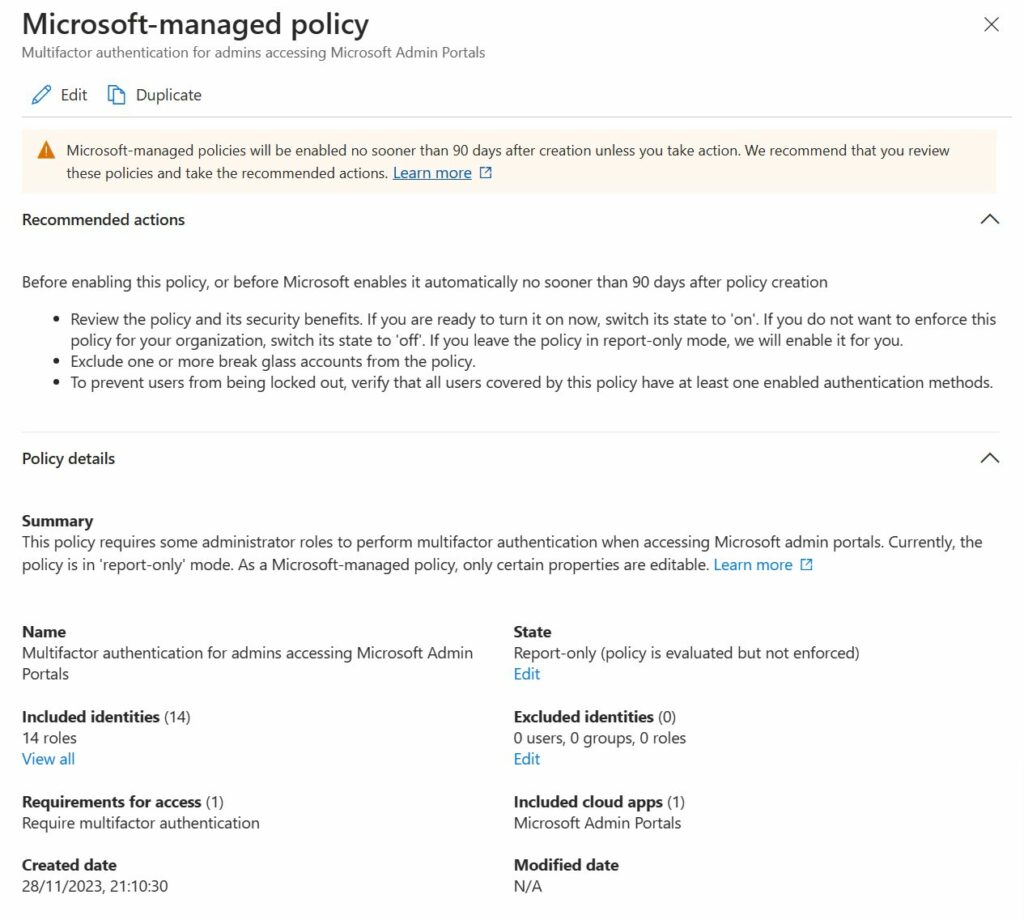
Notice that you can only change the State and add exclusions for who this policy should affect. You have the same options of you click “edit” on the top:
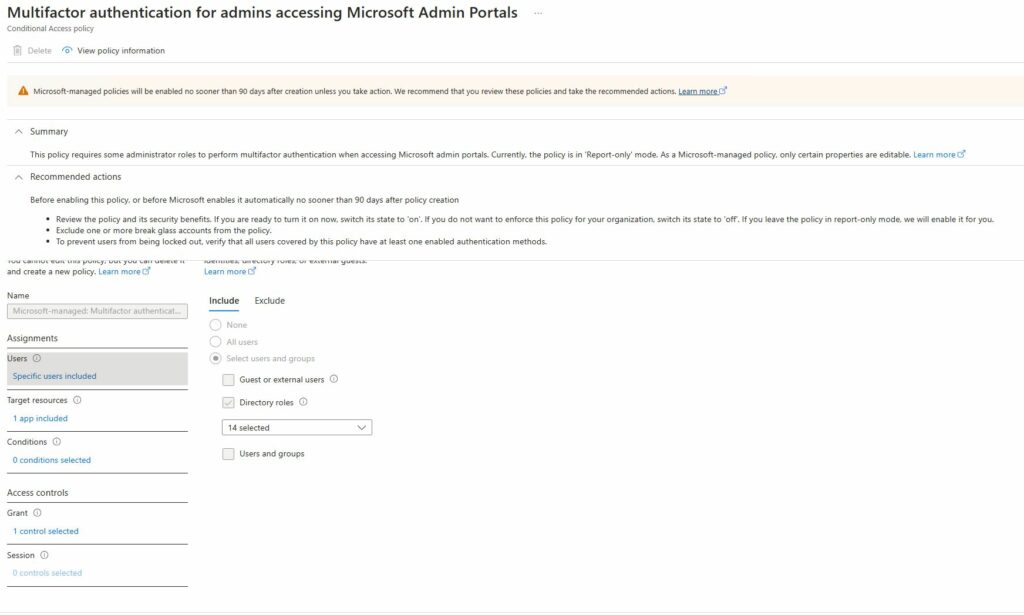
Most options are greyed-out here, leaving you with very few settings to change, but you can add exclusions and set the policy to off if you don’t want the policy at all. Your other option, located next to the “edit” button is “duplicate“. This will create a copy of the policy which you can change as you wish.
So what do I do now?
About the polices themselves: They are implemented with a lot of text from Microsoft that I think explains and summarize it all very well, so my first advice would be to read it through and not just dismiss these policies on a whim.
You can add any exclusions you need, like break-glass accounts, and worst-case set the policy to “off” so it won’t be enabled later.
As I wrote in the previous post on this topic: These policies are implemented for a reason, and you should absolutely go the extra mile to try to get MFA enabled across your organization. Security matters, and MFA is a crucial component of your cloud security!
I hope you found this post useful and that you will use this opportunity to implement better and more MFA coverage in your tenant.
Thank you
Discover more from Agder in the cloud
Subscribe to get the latest posts sent to your email.


